Regulatory responses to evolving technologies
28.12.2020Introduction
The digitization of societies and economies is continuously generating record amounts of data. Digitization is driven by increased and faster connectivity of people and things. Fibre to the home (FTTx) and fast mobile networks provide the opportunity to engage in digital activities, and social media and user-generated content provide the motivation for it. At the same time, more objects become “smart”, i.e. connected to the Internet to receive and send data. As a result of the explosion of data, new technologies have evolved that help to sift through data and derive value from combining and analysing large data sets. These technologies are often described in umbrella terms such as artificial intelligence (AI) and big data.
The new technologies require ICT regulators to reconsider the tools they deploy to facilitate fair competition in the ICT sector and protect consumers. New technologies also pose legal, ethical, and macroeconomic challenges. Central banks, consumer protection agencies, competition commissions, and ICT regulators scramble to assess the implications for their fields of responsibility. The implication is that roles of sector-specific regulators such as for the ICT sector, water, electricity, and banking, and subject-specific regulators such as a consumer protection agency or the competition commission may need to be redrawn and, in some cases, more specialized regulators may need to be established.
Figure 7.1 depicts how a sector specific ICT regulator is complimented by functional regulatory agencies that have responsibilities across all sectors of an economy.
Figure 7.1. The digital regulatory ecosystem
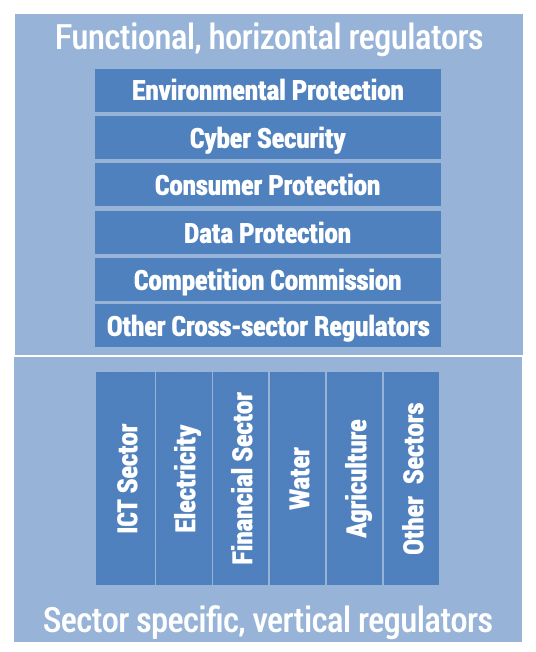
This chapter discusses the general trend in redefining the roles of the various regulatory authorities in response to cloud computing, AI, blockchain, big data, and the Internet of Things (IoT). While the desired outcomes – fair competition, consumer protection and economic development – remain the same, the approaches to achieve them are changing across time and differ between countries. This chapter aims to provide a framework to identify a suitable regulatory approach in response to arising technologies. The next section explains selected technologies in the context of the Internet value chain and evolving ICT sector business models. The last section discusses the evolving regulatory environment and options for allocating regulatory responsibilities to sectoral and/or functional regulators.
Evolving technologies
Blockchain, AI, big data, the cloud, and the IoT have in common that they all deal in one way or the other with data and that they facilitate new business models that may shift value creation within and between segments of the value chain. The IoT generates data (sensing and collecting), the cloud stores and processes data, big data derives data by combining large data sets, AI learns from data, including big data, and blockchain is a mechanism to reliably capture a data transaction history in a distributed manner (see Figure 7.2).
Figure 7.2. Linking technologies covered in this chapter
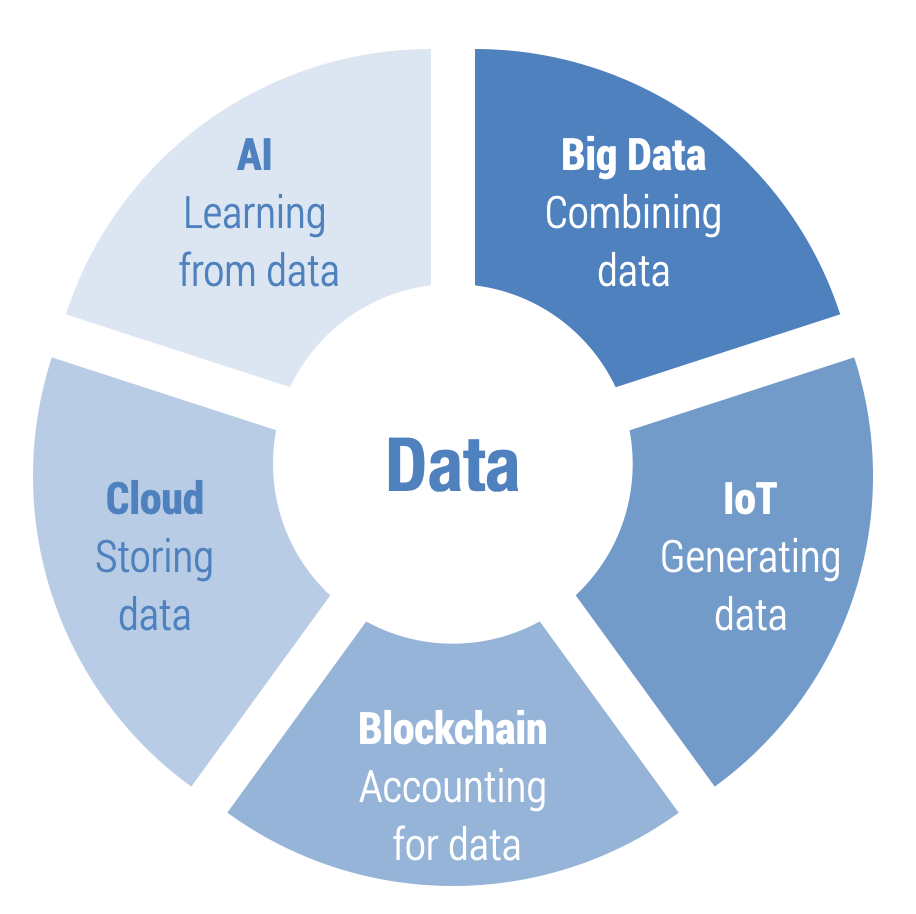
These technologies are different in that the IoT is subject to ICT sector regulations, while the others currently are not. While applications based on these technologies may be subject to ICT regulators or subject-specific regulators, such as data protection and consumer protection regulators and the entity in charge of cybersecurity, the technologies themselves are not. Cryptocurrencies, for example, use blockchain technology and the regulatory responsibility lies with central banks.
Cloud computing
Cloud computing converts IT infrastructure and software into services, delivered over the public Internet, including servers, storage, networking, software and data analysis. Cloud computing allows businesses to upscale and downscale the computing and networking power available to them within a few minutes. Cloud computing includes vendors that offer storage as a service, such as Dropbox and iCloud, and companies that focus on file transfer such as WeTransfer. Streaming services such as Netflix and YouTube and social media applications such as TikTok and Facebook all use cloud-based infrastructure.
The International Telecommunication Union (ITU) (2018b) defines cloud computing as a “[p]aradigm for enabling network access to a scalable and elastic pool of shareable physical or virtual resources with self-service provisioning and administration on-demand”.
In a sense, computing has come full circle. It started with centralized computing, with mainframe computers and dumb terminals, transitioned to individualized computing with personal computers (PCs) and laptops, and has now returned to centralized infrastructure (cloud computing) with smart terminals and devices, including smartphones and tablets. Cloud computing is part of the Internet value chain and regulatory issues are mainly related to data and consumer protection across multiple jurisdictions.
Internet of Things
The IoT is an umbrella term for technologies that allow objects to communicate. Ofcom defines it as the interconnection via the Internet of computing devices embedded in everyday objects, enabling them to send and receive data.[1] The IoT includes close range technologies, such as passive radio-frequency identification (RFID) and near-field communication (NFC); and technologies that cover large distances such as machine-to-machine (M2M) communication. M2M uses standard subscriber identity module (SIM) cards for identification and authentication on mobile networks. Figure 7.3 displays the number of SIM cards that are being used for IoT connectivity in the world. Ericsson’s Mobility Report (Ericsson, 2019) estimates that there will be 25 billion IoT devices in 2025.
Figure 7.3. Global connections, licensed cellular IoT (millions)
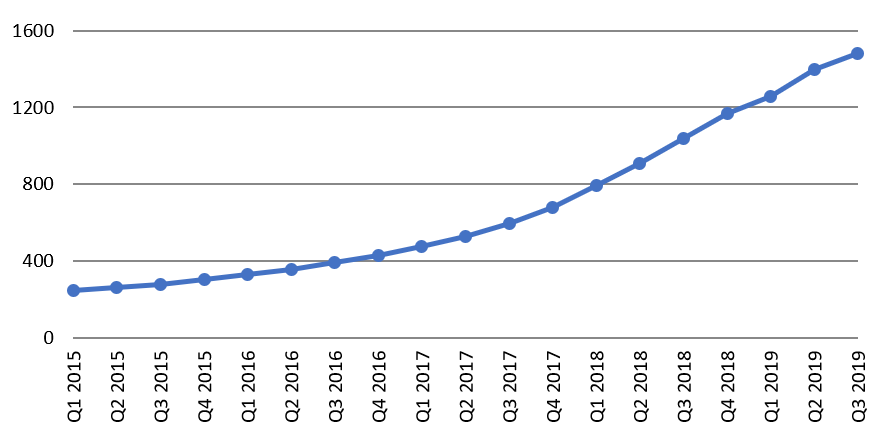
Source: GSMA Intelligence.
The IoT value chain is shorter than the Internet value chain, consisting of three to four segments (BEREC 2016):
- The IoT service provider is the company that incorporates the IoT in its products or services, for example, a car manufacturer or an electricity provider.
- The IoT connectivity provider could be a mobile operator or an Internet service provider (ISP) whose Internet connection is being used via Wi-Fi like Amazon’s Alexa or the Apple Watch.
- The IoT user purchases the IoT embedded product or service. Products and services can be combined or purchased separately. A car manufacturer could have a free tracking service included for a specific period of time or for the life of the car or charge for it separately.
The use of the IoT has several regulatory requirements:
- Spectrum use of the IoT needs to be regulated. Other than using SIM cards, IoT objects can communicate at different frequencies using Wi-Fi, NFC, or RFID. NFC can use the 300 MHz-3 GHz spectrum range, for example. RFID may be used in a low-frequency band of 125-134 kHz or at 13 MHz (ITU 2016).
- Competition issues revolving around customer lock-in resulting from fixed SIMs in devices. The costs of number portability in terms of switching mobile providers for IoT objects might be prohibitive. BEREC (2016) believes that the current number portability regulations might not be appropriate and new flexible approaches need to be developed.
- Data protection is paramount for the IoT. Who owns the data generated and what are the legal obligations for the data owner in terms of data use, storage, and liability for data breaches?
- Roaming may need to be addressed for IoT deployment using SIM cards. IoT devices may require permanent roaming across multiple jurisdictions (e.g. cars with built-in trackers). The question is whether roaming regulations apply to IoT objects. For the European Union (EU), for example, should IoT objects be subject to the principle of “roam like at home”?
- BEREC (2016) argues that if the number of roaming connections were to suddenly multiply, this might lead to access issues.
Addressing and numbering issues can be resolved by the adoption of eSIM cards that identify devices by international mobile subscriber identity (IMSI) and allow online switching of providers. The GSMA has produced a standard for eSIMs.[2]
The eSIM will bring new wholesale opportunities, including for companies that are not in the connectivity business. Private networks, e.g. in mines or ports, can have their own eSIMs, thus increasing security and controlling data use for specific applications. Hotel chains and hospitals could provide e-SIMs for their customers/patients with a set data allocation. IoT service providers can offer their products with data included and customers can top-up conveniently online, or change their provider while on holiday or when moving to another city.
Big data
Big data can be summarized as deriving value out of combining large data sets. Big data is a combination of various data sources and of data with different properties. UNSTATS (2015) describes the data characteristics in terms of volume, velocity, variety, the number of variables, veracity, selectivity, structure, and frequency (event-based or continuous). Big data is often described in terms of these “V” attributes (ITU 2014):
- Volume: Large data sets can come from a large number of sources such as call destination records (CDRs) from mobile phone calls and smart devices (IoT).
- Velocity: Velocity refers to the speed of data generation. Audited annual financial reports have a new record after 12 months. Supermarket sales records for a product can occur many thousand times a day.
- Variety: Data comes in different formats and types. It can be structured data from stock exchanges or unstructured data from text documents, emails, videos, audio recordings, and so on.
- Veracity: Veracity refers to the quality of data with some data being more reliable than others. An example of veracity of data is the difference between election opinion polls and election data, the latter having higher veracity.
- Value: Data has intrinsic value, which only materializes once the value is discovered and utilized.
Table 7.4. Sources of big data
| Data types | Examples |
| Administrative data | Administrative data are the data collected by the state, e.g. tax payments, birth certificates, social security numbers and contributions. |
| Survey data | The state conducts a serious of surveys throughout a year and some in cycles of five or 10 years. Examples include the census, labour force surveys, health surveys, and multipurpose household surveys. |
| High-frequency data | The private sector collects a wide range of high-frequency data. Examples include:
|
| Unstructured data | Text documents, videos, pictures are examples of structured data
Blogs and posts and other authored and unauthored online content |
| Geospatial data from satellites | Infrared imagery, to estimate population, for example |
Big data can be used to estimate ICT indicators for monitoring development targets in the ICT sector. It can also be used by mobile network operators (MNOs) to reduce churn, optimize networks, and provide better customer support:
- Churn prediction and individualized top-up packages and rewards are office tools to reduce churn. Acquiring a new customer is more expensive than retaining an existing customer. Big data, via the combination of customer usage, complaints, transactions, social media, and customer segmentation, can help identify customers that are likely to leave and design products/services that meet their specific needs (Deloitte 2015).
- Network optimization: operational expenses are a significant cost to operators. The upgrade to 5G could also require more base stations and managing the network will be more complex. In Nigeria, network and infrastructure maintenance costs for MTN are nearly 52 per cent. Big data analytics can be used to improve the performance of networks, by comparing real-time data with historical data (MapR 2020).
- Chatbots are widely used across the world by mobile operators for customer support. Chatbots can improve customer service.
Since big data involves the combination of different data sets, it is increasingly likely that the resulting data are able to identify individuals. Various data sets may also have different levels of consent and obligations for data owners, which heightens the need for stringent data protection laws.
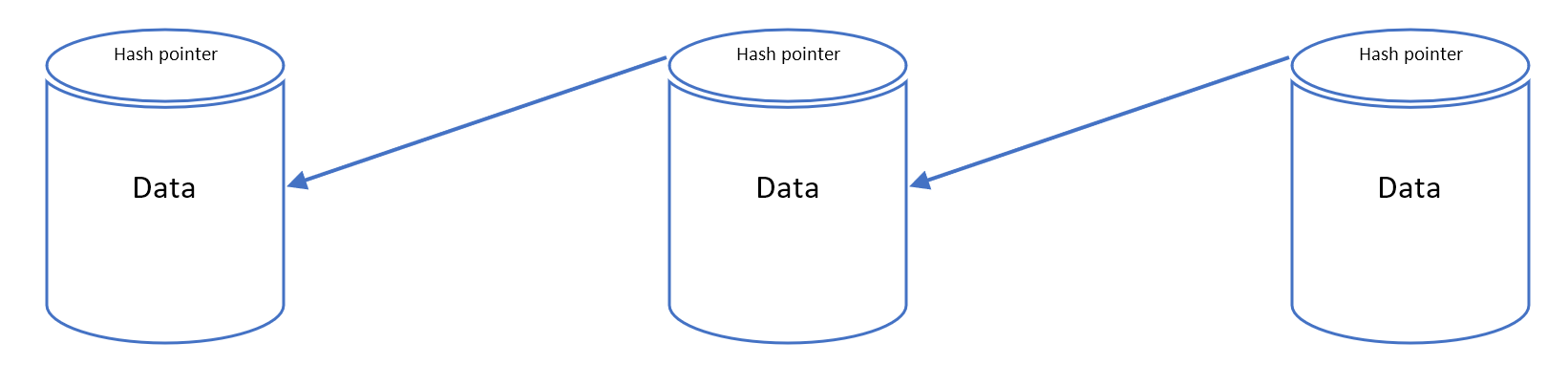
Blockchain
Blockchain is a technology that links records, called blocks, in a sequence using cryptography. Each record contains a set of information including a timestamp, who is participating in the transaction, and two unique identifying codes called a hash. A record contains the hash of the previous record as well as a hash for the current record, thus establishing a chain (see Figure 7.4). It is a type of distributed ledger which is composed of digitally recorded data arranged as a successively growing chain of blocks with each block cryptographically linked and hardened against tampering and revision (ITU 2019a). The distributed verification process makes blockchains resilient and nearly impossible to tamper with since there is no single point of failure. Even better, it becomes increasingly difficult to alter as further blocks are added to the chain.
An important distinction is between private and public blockchains. A public blockchain is also referred to as open or permissionless and allows anybody to join the network as a node and store a local copy of the ledger (Michels 2018). In contrast, in private blockchains (permissioned), data processing is restricted to a closed group of nodes.
Blockchain technology is not subject to any regulation in the same way that Hypertext Transfer Protocol Secure (HTTPS) or 3D printing is not subject to regulation. Blockchain is a technology that can be used for applications in a wide variety of sectors and with different properties and functionalities. A regulatory response may be needed depending on the sector and the use of blockchain technology.
Figure 7.5. Blockchain
Bitcoin, for example, is a decentralized digital currency that uses blockchain technology. Its use poses challenges with regard to preventing money laundering and fraud. Since the ledger is distributed across computer networks around the world, it would be difficult to stop transactions and/or inspect them only within one jurisdiction. Collaboration across jurisdictions is thus important.
Bitcoin was the first application of blockchain technology as a cryptocurrency. Since then many other cryptocurrencies have been launched but also non-currency applications are being tested. An ITU (2019b) report on distributed ledgers summarizes more than 50 blockchain use cases, including applications in the ICT sector. Recent examples of blockchain ICT sector implementation include:
- The Telecommunications Regulatory Authority of India (TRAI 2018) requires telecommunication to use blockchain-based technologies in creating a “do not disturb” registry to prevent spam. In the regulation, TRAI refers to distributed ledger technology (DLT) and blockchain is one type of DLT.
- Identity and data management: blockchain can be used to maintain trust and security among the billions of sensors that will be connected to the network (e.g. smart fridges, Wi-Fi routers, smart watches, and so on).
- Ofcom is holding a trial for blockchain technology to manage U.K. landline telephone numbers.[3] Blockchain is being trialled to improve the number portability process. Number ownership management and voice call routing can be created by capturing the parties to number porting and time swaps in a record (or block).
- The ID2020 Alliance[4] aims to develop a new global model for the design, funding, and implementation of digital ID solutions and technologies. Blockchain, along with biometrics, is being explored for this.[5]
- Deloitte (2016) released a report listing business opportunities for mobile operators and ISPs based on blockchain technologies. One application is to store cell-level network performance in blockchains to analyse network performance.
While regulatory concerns differ for each blockchain application, some issues, like data protection, will apply across most blockchain applications. Public blockchains allow anyone to see the entire transaction history, which may have data protection implications based on what information is recorded in the blocks. Private blockchains raise questions on the ownership of the data and the obligations for the data owners.[6]
Sector-specific regulation may be required for certain applications. Central banks are responsible for cryptocurrencies and would need to ensure compliance with money laundering regulations.
An example of the need for an ICT regulator to intervene may be when an operator abuses its market power by charging high prices based on its market power for services derived from a combination of blockchain-based digital IDs, eSIMs, and mobile money accounts. The emphasis must be on the abuse of market power. Existing legislation and regulation already prohibits the abuse of market power by dominant operators. In this instance, the tools to intervene in the market already exist and do not need to be reinvented.
Artificial intelligence
The Internet Society (2017) defines AI as “artificial creation of human-like intelligence that can learn, reason, plan, perceive, or process natural language”. It refers to systems that are designed to mimic human abilities to understand and solve problems. AI has many applications including predictive maintenance for cars and chatbots for customer support.
The ITU (2018a) notes that AI includes “five technologies”: computer vision, natural language processing, deep learning, robotics, and other automation systems. Limitations for deploying AI revolve around obtaining sufficiently large data sets, the ability to explain and generalize results from AI systems, and the risk of bias (ITU 2018a).
AI tools are what makes it feasible to process big data. The regulatory requirements are thus closely related to that of big data. However, further regulation may be needed because of the risk of bias that may stem from the data and algorithms used (McKinsey 2018). Additional steps may be required to resolve the risks of bias that go beyond the data and the algorithms.
There is a risk that the collected data have a selection bias or that it reflects societal biases and therefore hardwires injustices into a system. A famous example is the case of the U.S. Correctional Offender Management Profiling for Alternative Sanctions (COMPAS) algorithm that predicted black offenders to be 77 per cent more likely to reoffend than whites, with all other factors being similar.[7] Knowing the underlying bias in society, this could have been avoided by omitting race as one of the variables used to feed the learning algorithm. What is more important, though, is how this bias was discovered. It required an organization that was concerned about the outcomes and a mechanism to request the underlying data, which was done through a freedom of information request. The ability to detect biases will become more difficult with time as algorithms become more complex.
Regulators need to consider ways to address the “black-box” problem, where algorithms make decisions or give recommendations and the people affected by them have no way of understanding how these decisions and recommendations were derived (Deloitte 2018b). The EU, in response to these issues, formulated seven key requirements for AI regulation in a white paper that includes non-discrimination and fairness (European Commission 2020).
The General Data Protection Regulation (GDPR) of the EU, in Article 22, gives consumers the “right not to be subject to a decision based solely on automated processing, including profiling, which produces legal effects concerning him or her or similarly significantly affects him or her”.[8] This means that every consumer has the right to know what the data and underlying rationale are for making a decision, if it was an automated decision. For example, if a consumer is denied a loan based on an automated profile, the consumer can request the bank’s rationale.
However, the application of data protection and AI opens up a range of challenges. In the EU, the GDPR requires that data processors only use the minimum amount of data necessary to make the decision. The EU is trying to draw limits on the amount of data used and to limit the invasion of privacy. This is more complicated than it seems because the EU has not clearly defined what constitutes the required minimum. At the same time, other jurisdictions do not have this limitation so companies can use as much data as they like, potentially putting EU firms at a disadvantage and reducing innovation in the AI sector.
Similarly, every EU citizens has the right to see the raw data prior to profiling as well as the results after profiling (Article 15 of the GDPR). Unscrupulous companies could get access to the results of the profiling and reverse engineer the algorithms utilized by the initial company. These challenges show that considerable work has to be done to refine traditional regulatory tools to address the complexities of technologies like AI and their impact on issues like data protection.
The key question for the EU and regulators, in general, is whether the current data protection framework can create and maintain trust among suppliers and consumers. More stringent rules may be a competitive disadvantage on one level but, through the trust that is being built, achieve a competitive advantage on another level.
Smart capabilities and data protection
Technologies such as the IoT, AI and big data allow for the development of new capabilities for products and services. In Figure 7.5, IoT sensors monitor product usage, sending that data to the manufacturer for processing for updates or improvements. Manufacturers have a level of control over the features of the product. Tesla, for example, can change the battery range of a car via a software update, as it did for drivers caught in Hurricane Irma in 2017 (Liptak 2017). The combination of control and monitoring means that product performance can be improved or optimized. Monitoring, control, and optimization enable automation, which is dependent upon the learning capabilities of artificial intelligence.
Figure 7.5. Capability approach
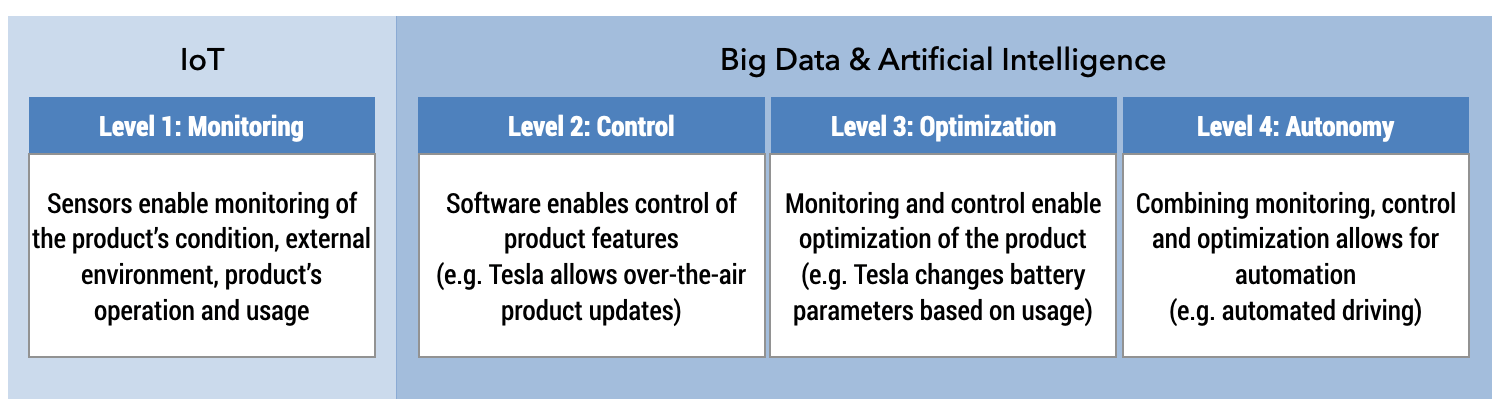
Source: Modified from Porter 2014.
The smart capabilities of products and services will create new models for collaboration that will need to address multiple, sometimes contradictory objectives: the protection of individual privacy versus the benefits of sharing knowledge across borders and industries.
There are already initiatives to foster collaboration across the value chain. Telecommunication and financial services have been collaborating on the regulation of mobile money. Similarly, Google and Apple’s recent announcement that they would partner to develop an open-source Bluetooth-based contact tracing technology for the COVID-19 pandemic that will require collaboration between public health authorities, ICT regulators, data protection agencies, and governments.
Moving data across jurisdictions has consequences for how to protect and share that data. Take a car company like Tesla that sells its cars entirely online, bypassing the traditional auto-dealer network, for example. Once the car is delivered to the customer, Tesla can monitor the status of the car and the car can either remotely call Tesla to schedule repairs or send a notification to the customer. It is not hard to imagine a scenario where usage data could be captured to provide tailored products to owners. Careful and calm driving behaviour could be rewarded by bigger discounts on car insurance. Pressing the accelerator aggressively by the driver could see an increase in insurance premiums because of the increased risk of an accident (see Figure 7.6).
Figure 7.6. Illustrative example of a Tesla sale across borders and third party use of data
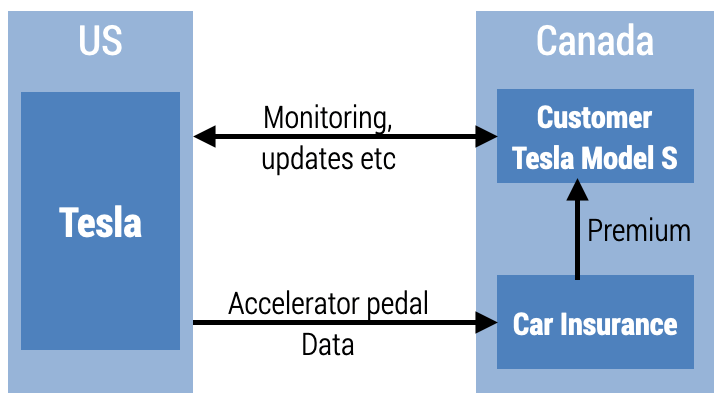
In this scenario, the data protection and privacy implications across so many different segments of the value chain require collaboration between different regulators. How should data be protected when they are collected using mobile networks (overseen by the ICT regulator), shared with insurance companies (overseen by the financial services regulator), and shared with car manufacturers (regulated by transport and safety authorities)? What recourse do consumers have if they do not want their car usage data shared with third parties like insurance companies? This complexity is exponentially increased in a scenario where a Canadian resident orders a Tesla from the United states online.
Data protection as the common denominator
AI, big data, and the IoT all require regulators to address five questions (Deloitte 2018b):
- Who owns the data that are being collected?
- What obligations does the owner of the data have in terms of storing and protecting that data?
- Can collectors of data price discriminate for users that agree that their data can be used versus those that have not provided consent?
- Do citizens have the right not to be evaluated by algorithms?
- May citizens request access to the data that were used to derive a decision or recommendation that affects them?
Essentially, data protection is about privacy.[9] Many countries consider the right to privacy to be a fundamental human right. More important, an actual or perceived lack of privacy results in consumers being resistant to new things (such as smart wearables like a smart watch) and generally risk-averse behaviour. Accenture (2016) found that 47 per cent of consumers had concerns about privacy and security preventing them from purchasing smart devices. Assuring consumers that their personal data belongs to them and they can control their use is a prerequisite for consumers to trust online transactions. When it comes to data protection, the first requirement is that the following high-level principles must exist in some form:
- Personal Information must be defined to relate to any information about an identifiable, living, natural person.
- Organizations[10] must be responsible for the personal information they collect.
- Organizations must state what they will use the personal information for and that those uses are reasonable.
- Organizations must use the personal information they need, not the personal information they want.
- Consumers[11] must know when and which organizations collect personal information about them and must consent to what organizations do with that data.
- Organizations must take reasonable steps to make sure the personal information is safe and, if there is a security breach, they need to inform consumers and help limit the damage.
- Organizations must do their best to ensure that the personal information they are entitled to have is of good quality.
- Some personal information, like biometric information and personal information about children, is more sensitive and must be subject to additional protection.
The data protection ecosystem consists of laws, institutions, and industry and consumer forums. Table 7.2 provides a framework to assess the data protection ecosystem for a country. Any questions answered with “no” provide an opportunity to improve the framework.
Table 7.2. Data protection ecosystem
| Data Protection Checklist | Yes | No | ||
| Does your country have a data protection law? | ||||
| Data Protection Law | Personal data | Does the definition of personal information include all aspects? Is personal data of organizations included? Is personal data of dead people included? | ||
| Accountability | Is it clear who the data controllers are and what they are responsible for? | |||
| Purpose | Are the lists of acceptable purposes consistent with other countries? | |||
| Minimality | Are organizations (or data controllers) forced to only use the personal information they need? | |||
| Notification/ openness | Are consumers (data subjects) told that their personal data are being used and given a chance to object to the use? What is the notification procedure in case of security breaches? | |||
| Security | Is security a standard requirement and is the recurring security loop explained? | |||
| Quality | Must organizations (data controllers) have a strategy in place to ensure that their data quality is good? | |||
| Sensitive personal data | Is sensitive personal data treated more carefully? | |||
| Data protection authority | Is there a specific independent body tasked with enforcing data protection and do they have enough funding and capacity? | |||
| International cooperation | Does the law set out that cooperation with international data protection authorities is required? | |||
| Direct marketing | Does the law regulate direct marketing without stopping it altogether? | |||
| Codes of conduct | Are there mechanisms to work with industry and concerned civic society groups to allow for self-regulation where appropriate? | |||
| Is data protection law adequate to cope with the way data are being used by evolving technologies? | ||||
| Does the regulating authority have sufficient expertise and funding to educate and enforce the data protection law? | ||||
| Does the regulating authority have sufficient jurisdictional power and international cooperation to operate in multiple countries with multiple regulating authorities? | ||||
| Does a freedom of information request mechanism exist? | ||||
As the data protection checklist highlights, the existence of appropriate legislation is necessary but not sufficient. The implementation of data protection legislation and regulation requires funding to both educate about and enforce data protection legislation. In developing countries, this is a significant challenge. The economic and social benefits that new technologies can bring are premised upon consumers having trust that their data are protected and that they have some level of control.
The evolving Internet value chain
Cloud computing, AI, big data analytics and blockchain are all part of the Internet value chain. Kearney[12] compiled an Internet value chain analysis in 2010 and the study was updated in 2016 for the GSMA.[13] The study distinguished five segments of the Internet value chain GSMA (2016a). For this Handbook, the Internet value chain has been extended to include the demand for digital services, which includes Internet access. Now the Internet value chain is seen not as a traditional set of sequential components but rather as a self-reinforcing circle (see Figure 7.7).
Figure 7.7. Internet value circle
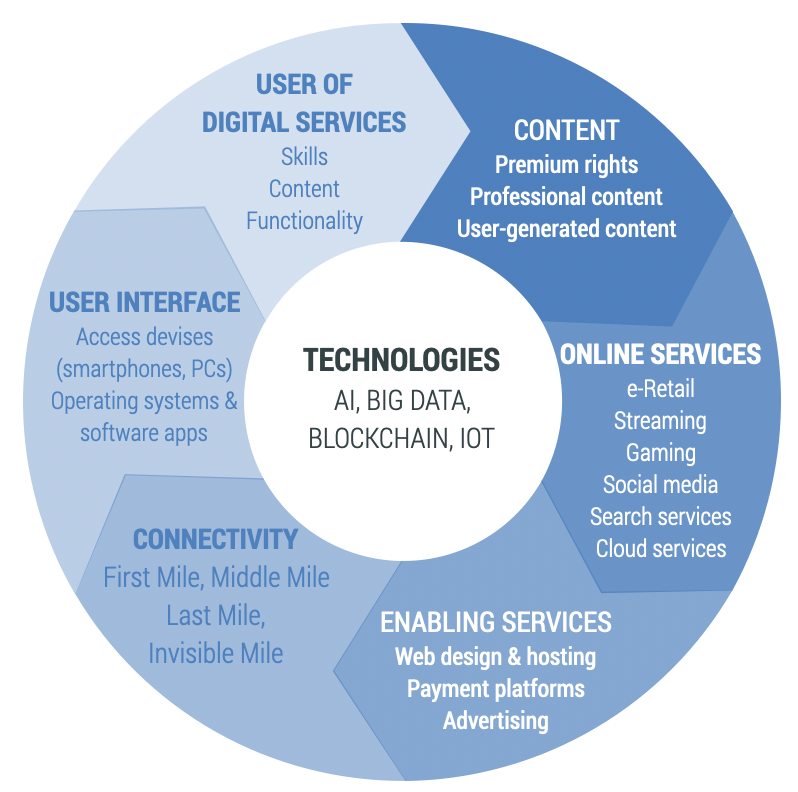
These six components are:
- Content rights: Includes premium rights with content that is produced professionally. It also includes user-generated content which is made available via social media platforms, such as YouTube, Twitter, Instagram, Vimeo, and Facebook, amongst others.
- Online services: Covers a wide range of services provided over the Internet including e-commerce; entertainment (gaming, gambling, video, music, publishing); search and reference services (Wikipedia, Google, Yahoo); social media and cloud services.
- Enabling technologies: Consists of essential services for the smooth running of the Internet such as the design and hosting of websites; payment platforms (credit cards, PayPal, MPESA), platforms enabling machine-to-machine (M2M) based services; advertisement platforms (ad exchanges and brokers).
- Connectivity: The connectivity segment can be distinguished between first, middle, last and invisible miles. The first mile refers to international data connectivity, i.e. how a country connects to the rest of the world via the Internet. The middle mile encapsulates national data connectivity including fibre networks and data centres. The last mile represents wireless or wired end-user access. The invisible mile captures regulatory and legislative factors that impact the ICT sector.
- User interface: Devices used by the end user to access the Internet include smart and feature phones; PCs, laptops and tablets; as well as digital TVs or digital set-top boxes. Operating software (OS) for these devices also falls into this segment as well as applications that run on top of the OS.
- Use of digital services: The demand for digital services depends, apart from disposable income and availability of connectivity, on skills of users, the desirability of content, and functionality.
In the past, the data flow was from content owners to the end user via the public Internet. Today, users create content through social media applications and other ways of uploading data, thus contributing to the content that is being consumed.
The Internet value chain combines various previously unrelated industries together on one platform, not just within a country but globally. To give just a few examples:
- Telephony started as voice calls, were enriched with texting, and now may be video calls over the public Internet.
- Shopping started at farm gates, moved to local markets, and now to online marketplaces.
- Shows and plays started on stages, moved to television and DVDs, and are now content on demand.
- Bookkeeping is increasingly automated via mobile apps and online services.
Traditionally TV and movie content had their own delivery channel. Today, the Internet is the unifying content delivery platform. The broadcasting business model remains the same, based on subscriptions or advertisements, while the mode of delivery is increasingly shifting to the IP platform. This has advantages for consumers who are now able to control what, when, and where to watch, instead of having to plan their entertainment time around the programming schedule of broadcasters.
Cloud computing, big data, blockchain, and AI enable value creation from the self-reinforcing Internet value circle. These technologies can profile users in terms of the content they consume and the content they produce, allowing online services to be individually targeted. The ability to provide targeted content, services, and advertising provides opportunities for a customized usage experience and new services and new business models. This also applies to the connectivity segment of the value chain, in particular for fixed-line and mobile operators, which are discussed in the next section.
Evolving business models in the ICT sector
The increasing digitization of the way we work and live also impacts the way we communicate. Instead of making traditional voice calls and sending 160 character SMS messages, people can communicate more conveniently, with full video and in groups using Internet applications. Services that were previously provided by MNOs are seeing competition from the public Internet. Voice calls and SMS have to compete with over-the-top (OTT) applications, such as Skype, WhatsApp, and Facebook Messenger. Cryptocurrencies based on blockchain technology may compete with mobile money. The business models of domestic connectivity providers need to adjust to these new services, as do regulators, who have to reconsider their scope of responsibilities.
MNOs are mobile ISPs and data are the primary source of revenues. The mobile business model will follow that of fixed-line operators, which started out as voice service providers but now make their money mostly from data connectivity, either retail or wholesale. Over the past two decades, the majority of MNO investment has gone into data networks. The transition from a voice and SMS to datacentric-business model is inevitable (see Table 7.3). MNOs will eventually entirely become mobile Internet access providers, distinguishing their products by speed and quality of service, and competing with other forms of access, such as Public Wi-Fi and connectivity in places of work, study and home. MNOs will no longer charge for voice and SMS, only for bandwidth and/or data consumption. The mobile ISP business model can also be described as a data-centric or a digital business model. Figure 7.8 illustrates this transition.
Figure 7.8. Illustrative trends towards digital mobile business models
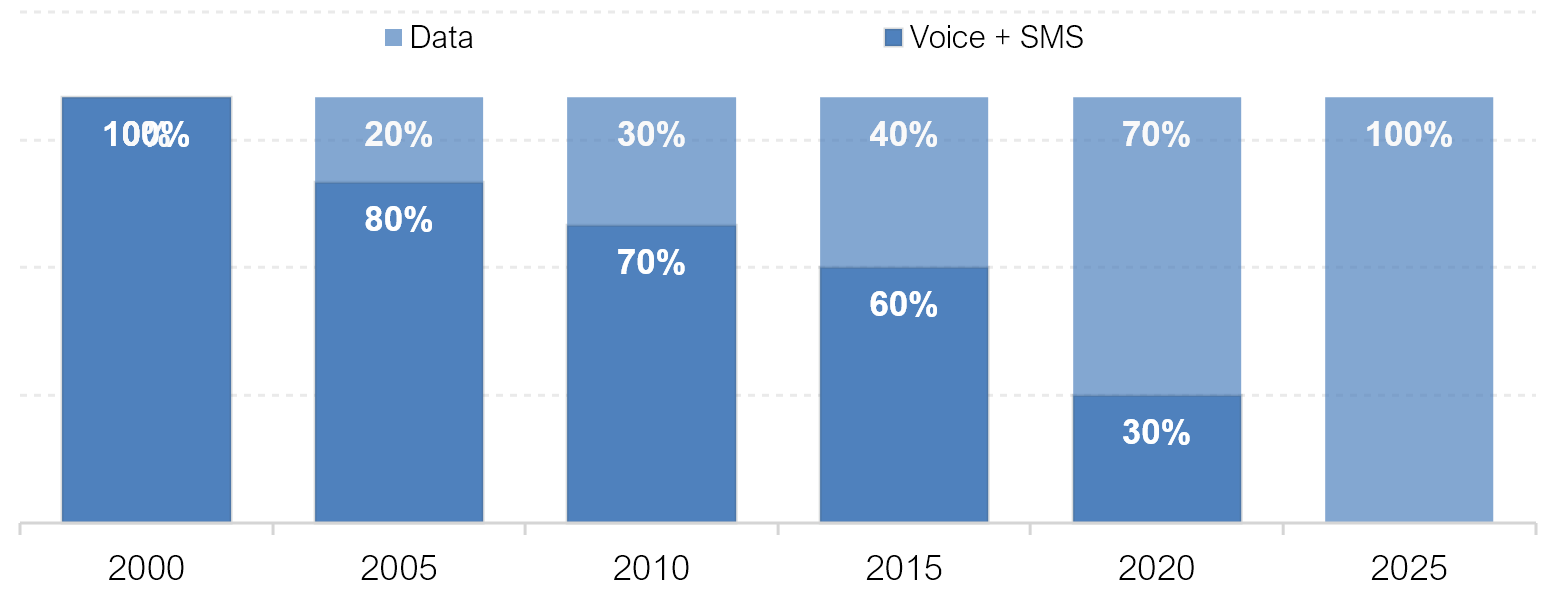
Source: Esselaar and Stork 2019.
Apart from competitive pressure, the trend described in Figure 7.8 also depends on smartphone penetration and 3G+ network coverage. The migration to a digital mobile business model will take longer for countries that have little 3G, 4G, and public/private Wi-Fi coverage and low smartphone penetration. Insufficient 3G+ network coverage is one of the main reasons why some mobile operators struggle to generate enough data revenues to compensate for declining voice and SMS revenues.
Table 7.3. The evolving digital business model is inevitable
| Analogue mobile | Digital mobile | |
| Business model | Service | Connectivity |
| Metric | Minutes and SMS | Bandwidth or throughput |
| Cost sensitivity | Distance, duration and location matter | Time, distance and location insensitive |
| Billing | Access and usage billing: Detailed billing systems for voice and SMS that can distinguish between off-net/on-net, peak/off-peak | Simple access billing |
| Traffic monitoring | Detailed traffic monitoring as part of the billing system | Usage monitoring limited to data use |
| Postpaid subscribers | Detailed vetting to reduce risk or revenue loss and expenses that arise from call termination and subsidized handsets |
|
| Network infrastructure | GSM 1G and 2G | 2.5G, 3G, 4G, 5G |
Source: Esselaar and Stork 2019.
The digital business model is all about knowing the customer. The actual battle is not that of cannibalization of one product for another, i.e. replacing voice and SMS with data revenues, but one of maintaining information on subscriber leadership. For years, MNOs were in the lead, knowing where their customers were in space and time, whom they communicated with and when. While this information is still available to MNOs, social media and online shopping provide a more potent and detailed information source. The information that Amazon and Facebook have about a customer is likely to be more economically valuable than the information that an MNO has about the same customer. To enter this market is a business decision, not a regulatory decision.
EBITDA margins along the Internet value chain show that end-user access is still a profitable business. More important than the size of each segment in terms of revenues is the profitability of major players in each of the value chain segments. Table 7.4 displays the earnings before interest, taxes, depreciation, and amortization (EBITDA) margin for selected players for each of the value chain segments. On average, EBITDA margins for connectivity are higher than the other segments of the value chain. It would be difficult to argue that MNOs are facing more adverse conditions than other segments. The variance of EBITDA margins between segments also shows that each segment has its own value proposition, investment criteria, and returns. Netflix is, for example, much more profitable than Disney.
Table 7.4. EBITDA margin along the value chain based on audited financial statements (%)
| Segment | Company | 2016 | 2017 | 2018 |
| Content rights | Netflix | 60 | 61 | 59 |
| Warner Media | — | — | 18 | |
| Disney | 30 | 30 | 29 | |
| Fox Corporation | — | — | 22 | |
| Online services | Amazon | 9 | 9 | 12 |
| Alphabet | 33 | 30 | 26 | |
| 53 | 57 | 52 | ||
| Enabling technologies | Cisco | 30 | 30 | 31 |
| Akamai | 41 | 37 | 40 | |
| Connectivity | Airtel Group | 35 | 38 | 37 |
| Etisalat | 50 | 50 | 49 | |
| Maroc Telecom Group | 48 | 49 | 50 | |
| MTN Group | 35 | 33 | 35 | |
| Ooredoo | 41 | 42 | 41 | |
| Sonatel | 49 | 47 | 45 | |
| Safaricom | 42 | 48 | 48 | |
| Vodacom Group | 38 | 38 | 38 | |
| Average Connectivity | 42 | 43 | 43 | |
| User interface | Apple | 33 | 31 | 31 |
| Samsung | 24 | 31 | 35 |
Source: Esselaar and Stork 2019.
As MNOs transition into a fully datacentric model, they can expect their profit margins to decline to the levels of other segments of the value chain. The transition to a datacentric model also means less need for ICT sector-specific regulation. With the exception of the radio spectrum, telecommunication regulation will become less sector specific over time.
Summary
Evolving business models and technological progress mean that regulatory tools and institutional arrangements may have to change and regulatory oversight may be shifted to new or different organizations (see Figure 7.9). While the line ministry was an adequate supervisory body for landline monopolies, sector-specific regulators were needed as soon as ISPs and MNOs entered the market. The transition to an all-digital, all-IP world means that laws, policies, and regulations need to evolve to maintain fair competition. This has consequences for national regulatory institutions including ICT and broadcasting regulators, competition commissions, and consumer protection agencies. Big data, AI, and the IoT are driving the need for a redesign of the regulatory landscape because these technologies are able to combine, analyse, and utilize disparate sources of data, providing insights that do not only apply to one sector but across sectors and not only to one jurisdiction but to many. New, highly specialized regulatory institutions are increasingly required to deal with the issues that arise from the globalization of personal data, especially in terms of protecting personal data and resolving consumer disputes.
Figure 7.9. Changing regulatory approaches over time
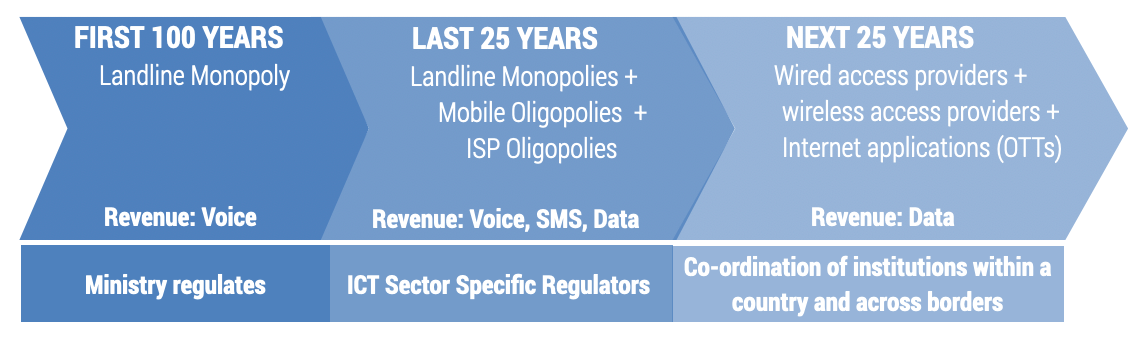
Any application based on the technologies in this chapter is subject to horizontal regulation by agencies responsible for consumer protection, data protection, competition, cybercrime, and so on. Whether or not ICT sector-specific regulatory oversight is warranted depends on the functionalities of the applications and how they are used in a sector. The priority must be to have a robust horizontal regulatory ecosystem in place. This may require updating laws and establishing new agencies.
Given the cross-border nature of the Internet value chain, in particular of online services, collaboration and harmonization across jurisdictions is key to facilitate the digitization of economies and societies and the benefit of economic growth and social development that this brings.
Notes
- Definition of IoT, https://www.ofcom.org.uk/manage-your-licence/radiocommunication-licences/internet-of-things. ITU Recommendation ITU-T Y.2060 provides an overview of the Internet of things (IoT) and more detailed definition: “Internet of things (IoT) is defined as a global infrastructure for the information society, enabling advanced services by interconnecting (physical and virtual) things based on existing and evolving interoperable information and communication technologies.NOTE 1 – Through the exploitation of identification, data capture, processing and communication capabilities, the IoT makes full use of things to offer services to all kinds of applications, whilst ensuring that security and privacy requirements are fulfilled.NOTE 2 – From a broader perspective, the IoT can be perceived as a vision with technological and societal implications.” https://www.itu.int/ITU-T/recommendations/rec.aspx?rec=y.2060. ↑
- Embedded SIM or embedded universal integrated circuit card (eUICC), https://www.gsma.com/iot/embedded-sim/. ↑
- Ofcom, How Blockchain Technology Could Help to Manage U.K. Telephone Numbers, https://www.ofcom.org.uk/about-ofcom/latest/features-and-news/blockchain-technology-uk-telephone-numbers. ↑
- https://id2020.org/alliance. ↑
- ID2020: Digital Identity with Blockchain and Biometrics, https://www.accenture.com/us-en/insight-blockchain-id2020. ↑
- A report by the ITU (2019b) provides more details on regulatory implications of specific applications of blockchain technology. ↑
- How We Analyzed the COMPAS Recidivism Algorithm, https://www.propublica.org/article/how-we-analyzed-the-compas-recidivism-algorithm. ↑
- https://gdpr-info.eu/art-22-gdpr/. ↑
- See Chapter 5 on “Data protection and trust” for an examination of on the regulatory aspects of data protection. ↑
- Organizations and individuals can collect data. In legal terms, organizations/individuals that collect data are referred to as data controllers. The term “data controller” comes from the EU’s GDPR and is defined as “a person, company, or other body that determines the purpose and means of personal data processing (this can be determined alone, or jointly with another person/company/body)” https://www.atinternet.com/en/glossary/data-controller/. ↑
- In legal terms, a consumer is known as a “data subject”. The term data subject comes from the EU’s GDPR and is defined as “any individual person who can be identified, directly or indirectly, via an identifier such as a name, an ID number, location data, or via factors specific to the person’s physical, physiological, genetic, mental, economic, cultural or social identity. In other words, a data subject is an end user whose personal data can be collected” (https://www.atinternet.com/en/glossary/data-subject/). ↑
- Internet value chain economics, https://www.kearney.com/communications-media-technology/article?/a/internet-value-chain-economics. ↑
- https://www.gsma.com/publicpolicy/wp-content/uploads/2016/09/GSMA2016_Report_TheInternetValueChain.pdf ↑
References
Accenture 2016. Igniting Growth in Consumer Technology. https://www.accenture.com/t20151231t013104__w__/us-en/_acnmedia/pdf-3/accenture-igniting-growth-consumer-technology.pdf.
BEREC. 2016. BEREC Report on Enabling the Internet of Things. BoR (16) 39. https://berec.europa.eu/eng/document_register/subject_matter/berec/reports/5755-berec-report-on-enabling-%20the-internet-of-things.
Deloitte. 2015. Opportunities in Telecom Sector: Arising from Big Data. https://www2.deloitte.com/content/dam/Deloitte/in/Documents/technology-media-telecommunications/in-tmt-opportunities-in-telecom-sector-noexp.pdf.
Deloitte 2016. Blockchain @ Telco: How Blockchain Can Impact the Telecommunications Industry and its Relevance to the C-Suite. https://www2.deloitte.com/content/dam/Deloitte/za/Documents/technology-media-telecommunications/za_TMT_Blockchain_TelCo.pdf.
Deloitte 2018a. “Regulating the Future of Mobility: Balancing Innovation and the Public Good in Autonomous Vehicles, Shared Mobility, and Beyond”. Deloitte Insights, December 21, 2018. https://www2.deloitte.com/us/en/insights/focus/future-of-mobility/regulating-transportation-new-mobility-ecosystem.html.
Deloitte 2018b. “The Future of Regulation: Principles for Regulating Emerging Technologies”. Deloitte Insights, June 19, 2018. https://www2.deloitte.com/us/en/insights/industry/public-sector/future-of-regulation/regulating-emerging-technology.html.
Deloitte 2018c. The Regulator’s New Toolkit: Technologies and Tactics for Tomorrow’s Regulator. https://www2.deloitte.com/content/dam/insights/us/articles/4539_Regulator_4-0/DI_Regulator-4-0.pdf.
Deloitte 2018d. Government Trends 2020: What are the Most Transformational Trends in Government Today? Deloitte Insights, June 24, 2019. https://www2.deloitte.com/us/en/insights/industry/public-sector/government-trends/2020/government-data-ai-ethics.html.
Ericsson 2019. Ericsson Mobility Report. https://www.ericsson.com/4acd7e/assets/local/mobility-report/documents/2019/emr-november-2019.pdf.
Esselaar, S. and C. Stork. 2019. “Evolving Business Models are Driven by OTT Applications”. Paper presented at the ITU Study Group on OTT, Geneva, September 2019. https://researchictsolutions.com/home/wp-content/uploads/2019/11/RIS-evolving-business-models.pdf.
European Commission. 2020. White Paper on Artificial Intelligence: A European Approach to Excellence and Trust. COM(2020) 65 final. https://templatearchive.com/ai-white-paper/ .
Internet Society. 2017. Paths to Our Digital Future. https://future.internetsociety.org/2017/wp-content/uploads/sites/3/2017/09/2017-Internet-Society-Global-Internet-Report-Paths-to-Our-Digital-Future.pdf.
ITU (International Telecommunication Union). 2014. “The Role of Big Data for ICT Monitoring and for Development”, In Measuring the Information Society Report 2014, Geneva: International Telecommunication Union. https://www.itu.int/en/ITU-D/Statistics/Documents/bigdata/MIS2014_Chapter5.pdf.
ITU (International Telecommunication Union). 2016. Trends in Telecommunication Reform: Regulatory incentives to Achieve Digital Opportunities. Geneva: International Telecommunication Union. https://www.itu.int/pub/D-PREF-TTR.17-2016.
ITU (International Telecommunication Union). 2017. Global ICT Regulatory Outlook 2017. Geneva: International Telecommunication Union. Geneva: International Telecommunication Union. https://www.itu.int/en/ITU-D/Regulatory-Market/Pages/Outlook/2017.aspx.
ITU (International Telecommunication Union). 2018a. Assessing the Economic Impact of Artificial Intelligence. ITU Trends: Issue Paper No.1. Geneva: International Telecommunication Union. https://www.itu.int/dms_pub/itu-s/opb/gen/S-GEN-ISSUEPAPER-2018-1-PDF-E.pdf.
ITU (International Telecommunication Union). 2018b. Cloud Computing Standardization Roadmap. ITU-T Y.3500-series. Geneva: International Telecommunication Union. https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-Y.Sup49-201811-I!!PDF-E&type=items.
ITU (International Telecommunication Union). 2019a. Distributed Ledger Technology Terms and Definitions. Technical Specification FG DLT D1.1. Geneva: International Telecommunication Union. https://www.itu.int/en/ITU-T/focusgroups/dlt/Documents/d11.pdf.
ITU (International Telecommunication Union). 2019b. Distributed Ledger Technology: Regulatory Framework. Technical Paper HSTP.DLT-RF. Geneva: International Telecommunication Union. https://www.itu.int/dms_pub/itu-t/opb/tut/T-TUT-DLT-2019-RF-PDF-E.pdf.
Liptak, Andrew. 2017. “Tesla Extended the Range of Some Florida Vehicles for Drivers to Escape Hurricane Irma”. The Verge, September 10, 2017. https://www.theverge.com/2017/9/10/16283330/tesla-hurricane-irma-update-florida-extend-range-model-s-x-60-60d.
MapR. 2020. MapR Guide to Big Data in Telecommunications. https://mapr.com/whitepapers/data-convergenece-in-telecommunications/assets/data-convergenece-in-telecommunications.pdf. Accessed April 24, 2020.
McKinsey. 2018. Notes from the AI Frontier: Insights from Hundreds of Use Cases. https://www.mckinsey.com/~/media/mckinsey/featured%20insights/artificial%20intelligence/notes%20from%20the%20ai%20frontier%20applications%20and%20value%20of%20deep%20learning/notes-from-the-ai-frontier-insights-from-hundreds-of-use-cases-discussion-paper.ashx.
Michels, Johan David. 2018. “Blockchain and Telecoms”. InterMEDIA, (46) 4. https://ssrn.com/abstract=3324482.
Porter, M. and James E. Heppelmann. 2014. “How Smart, Connected Products Are Transforming Competition”. Harvard Business Review, November 2014. https://hbr.org/2014/11/how-smart-connected-products-are-transforming-competition.
TRAI (Telecom Regulatory Authority of India). 2018. “Information Note to the Press”. Press Release No. 58/2018. https://www.trai.gov.in/sites/default/files/PRNo.5829052018.pdf.
UNSATS. 2015. Deliverable 2: Revision and Further Development of the Classification of Big Data. United Nations Global Working Group on Big Data for Official Statistics Task Team on Cross-Cutting Issues. https://unstats.un.org/unsd/trade/events/2015/abudhabi/gwg/GWG%202015%20-%20item%202%20(iv)%20-%20Big%20Data%20Classification.pdf.
Last updated on: 26.04.2023