Enhancing the protection and cyber-resilience of critical information infrastructure
17.06.2021Introduction
In today’s highly connected, interdependent world, several critical infrastructure (CI) sectors, such as health care, telecommunications, finance, energy, among others, increasingly rely on information technology (IT) and operational technology[1] (OT) systems. Not only are these critical information infrastructures (CII) in their own right, for example, cloud-based technology services, but they also underpin many other critical services, for example, water supply, power grids, and fuel pipeline supply. The malfunctioning or disruption of these critical services could cause significant social and economic harm and even loss of life. For this reason, key stakeholders from the CI/CII ecosystem should adopt a strong cybersecurity posture to ensure the protection and cyber-resilience of CI/CII sectors and services.
To achieve this goal, CII operators should allocate sufficient resources to adopt and implement cyber-tools and internationally recognized security standards (at least as good practice) and also comply with domestic CIIP policy and legal frameworks (if any) to protect their information and communications technology (ICT) infrastructures and data from increasing cyber-risks and attack vectors.[2] On the other hand, governments, through coordinating authorities, should also allocate sufficient resources to implement and monitor critical information infrastructure protection (CIIP) policy and regulatory frameworks with clear legal mandates, roles and responsibilities, security requirements, and legal obligations to ensure that the CII’s sectors and services are adequately protected.
This article aims to guide CII ecosystem stakeholders, including national CIIP coordinating authorities, ICT regulators, network and services providers, Internet services providers (ISPs), among others, to better understand not only the essential aspects of the protection of CII’s sectors and services but also the regulatory aspects, such as identification of the CII, CIIP regulatory models, the role of CII coordinator, and a number of security requirements and legal obligations which are being implemented in several countries worldwide.
Background
Early in the 2000s, the concept of critical infrastructure protection (CIP) became a major concern for many countries, especially after the terrorist attacks in the United States (2001), in Spain (2004), and in the United Kingdom (2005). These attacks had a major impact not only on how critical services were delivered (for example, air and underground transportation) but also on the perception of national security. Following these attacks, both U.S. and European Union (EU) authorities were forced to redefine the concept of CI and establish robust security and legal measures, such as the adoption of the Patriot Act of 2001[3] and Directive 2008/114/EC,[4] to ensure the protection of CI sectors and services.
Critical information infrastructure protection (CIIP) was first coined in the 2000s when experts decided to find solutions for the protection of IT and OT interlinkages between different CI sectors and services. This convergence and interconnection between IT and OT systems (and now with Industrial Internet of Things’ components) have created a new set of cyber-risks and vulnerabilities, representing a crucial security issue worldwide. This situation requires that CII operators and CI/CII stakeholders at large, including ICT regulators, adopt a number of coordinated efforts and enhance their cybersecurity posture to protect CI/CII sectors and services.
What is critical infrastructure?
There is no universally agreed definition of critical infrastructure. Each country defines CI based on its current needs and priorities, so there are different approaches to defining its scope. When comparing the sets of CI sectors of different countries, one may find a similar base set of CI but also major differences (TNO 2017). A particular CI service might be vital to one country (for example, the Panama Canal) but not to another country.
CI is generally defined as those sectors, including subsectors, services, and assets (see box 1 below), which are vital for the functioning and resilience of society (for example, energy, telecommunications, health, financial services) and that their partial or total disruption or destruction would result in a significative negative impact not only to the national security but also to the national economy and social well-being of people.

Source: Centre for the Protection of National Infrastructure, Critical National Infrastructure.
In 2019, the Organisation for Economic Cooperation and Development (OECD) published a CI-related report which revealed that about 90 per cent of its members had identified their national CI sectors and that the scope of their CI definitions varied from one country to another (OECD 2019). Some countries stress the importance of protecting their CI sectors from an economic and social well-being perspective, while other countries from a national security view. A third group of OECD countries combined those two approaches into their CI definition (for example, the United Kingdom).
Critical Infrastructure Sectors
Figure 1. Energy sector, subsector, critical services and assets
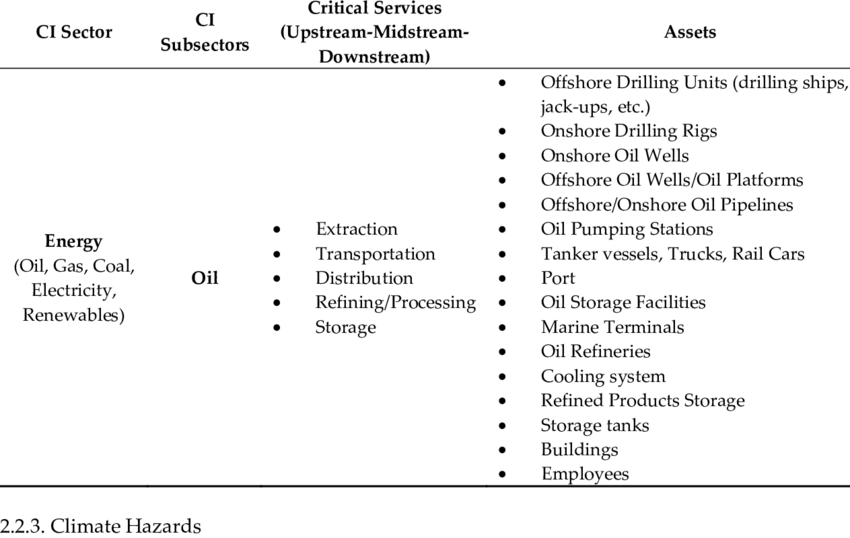
The nature of national CI sectors varies across countries because the identification process is based on regular national risks and prioritization assessments. Some countries have a large number of CI sectors. For example, the United States has 16 sectors (see figure 2),[5] Malawi has 15,[6] the United Kingdom has 13,[7] and Australia has 8,[8] while other countries have identified fewer CI sectors, for example, Brazil has 5 CI sectors.[9] Common to all these countries is that telecommunications and energy are part of their national CI sectors.
Figure 2. United States: 16 critical infrastructure sectors.
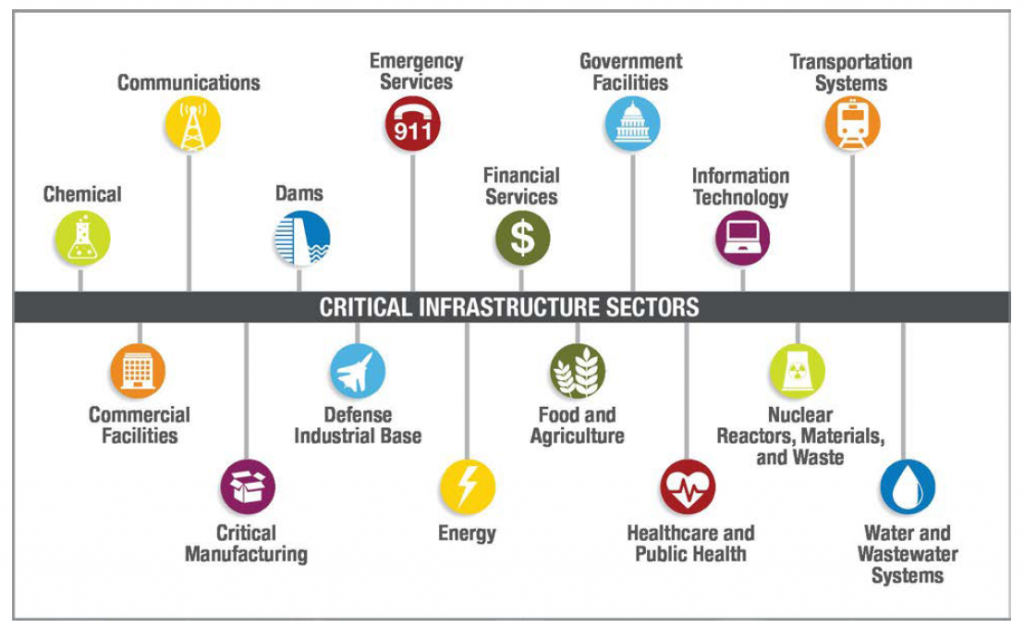
Source: https://etn-peter.eu/2021/04/06/basics-of-any-critical-infrastructure/.
According to the OECD’s 2019 report, energy, information and communications technology (ICT), transportation, health, water, and finance are the most CI-designated sectors across OECD countries, with the nuclear and the defence sectors being the least CI-designated. Each country has its own needs and priorities which will determine national CI sector identification (see table 1). For instance, in the United States, the number of CI sectors has changed over time. In 1996, there were only eight sectors (EO-13010), but in 1998, Presidential Decision Directive 63 identified 15 CI sectors. In 2001, Executive Order 13228 reduced the number of sectors to nine, and today there are 16.[10]
Table 1. List of CI sectors in the United States, Canada, Japan, Malawi, Singapore, and United Arab Emirates
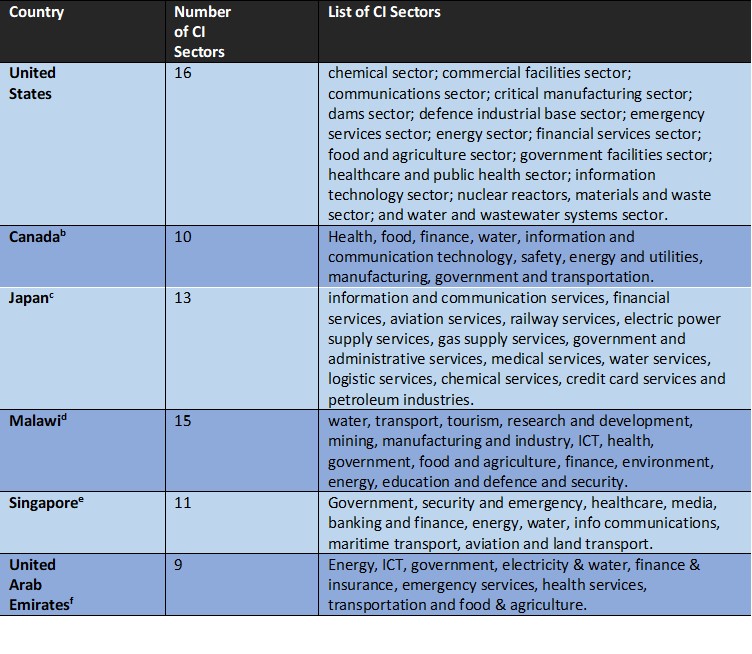
Source: a. CISA. 2021. Critical Infrastructure Sectors. https://www.cisa.gov/critical-infrastructure-sectors; b. OECD. Canada’s National Strategy for Critical Infrastructure. https://www.oecd.org/governance/toolkit-on-risk-governance/goodpractices/page/canadasnationalstrategyforcriticalinfrastructure.htm; c. CIPEdia. 2021. Critical Infrastructure Sector. https://websites.fraunhofer.de/CIPedia/index.php/Critical_Infrastructure_Sector#Japan; d. Malawi CMM review 2020 (draft stage); e. Cybersecurity Act of Singapore. 2021. https://www.ifaq.gov.sg/csa/apps/fcd_faqmain.aspx?qst=hRhkP9BzcBImsx2TBbssMsxu7lqt6UJK70a1wAEVmydAK28G3buDOq3D6Gn5MnNjBwWSfr%2FWJXJ3SLLP8N%2FrnF%2Bs5nglrzZ9fu3D0OBX%2BiPiNj7VlFzrCXdbHE4Zka6%2FnR9LPji1JebIhMUd1OYjZpkRJ3VrLBAhOFXeXkjpiEhbvuyWgKMBTpDedU4WBscvIptl6Q7j3vq5Edr%2Bp%2BSzHtIZAJntu9NEWSsGKvAcuMU%3D#FAQ_2109834; f. Telecommunications and Digital Government Regulatory Authority (2021). National Cybersecurity Strategy. https://www.tdra.gov.ae/en/national-cybersecurity-strategy.aspx.
What is critical information infrastructure?
Like CI, there is no universally agreed definition of critical information infrastructure (CII). CI and CII are often used interchangeably, but strictly they are not the same. There are substantial differences that must be clarified so that policy-makers, regulators, and other stakeholders better understand both concepts and the associated regulatory activities.
Box 2. Definitions of CII.

Source: a. Commission of the European Communities. 2005. Green Paper on a European Programme for Critical Infrastructure Protection. https://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=COM:2005:0576:FIN:EN:PDF; b. TNO. 2017. The GFCE-Meridian Good Practice on Critical Information Infrastructure Protection for Governmental Policy-Makers. https://www.meridianprocess.org/siteassets/meridian/gfce-meridian-gpg-to-ciip.pdf; c. African Union. Convention on Cyber Security and Personal Data Protection. https://au.int/sites/default/files/treaties/29560-treaty-0048_-_african_union_convention_on_cyber_security_and_personal_data_protection_e.pdf; and, d. OECD. 2019.
The GFCE-Meridian report on CIIP (TNO 2017) states that CII comprises both:
- Critical information and (tele) communication infrastructures (for example, mobile telecommunications services, Internet exchange points, domain name services, cloud computing), and,
- Critical information and communication systems cover information technology (IT) and operational technology (OT) systems and networks – both converging at a faster pace. Those two technologies are used to operate certain CI assets and facilities. For instance, industrial and automation control systems monitor and control critical cyber-physical processes (for example, remote operation of oil pipeline valves) and administrative and logistic systems (TNO 2017) (see figure 3.)
Figure 3. Differences between critical infrastructure and critical information infrastructure.
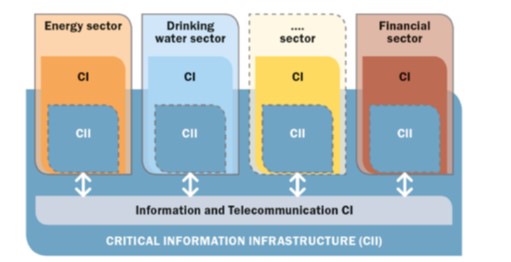
Note: The CII enclose 1) the information and telecommunication CI, and 2) the CII components in CI (e.g., control systems.
Source: TNO 2017.
As shown in figure 3, CII comprises both ICT as CI alone and the cross-CI sector aspect because some CI sectors, such as energy, drinking water supply, and finance, use the same technologies to operate; and therefore, they also are exposed to cyber-risks and vulnerabilities in most critical processes. The reliance on ICT systems has brought more complexity, (inter)dependencies, and vulnerabilities, thus increasing the risk and attack opportunities.
For more clarity, the GFCE-Meridian report on CIIP (TNO 2017) defines CII and CIIP as follows:
Critical Information Infrastructure (CII): “Those interconnected information and communication infrastructures which are essential for the maintenance of vital societal functions, (health, safety, security, economic or social well-being of people) – the disruption or destruction of which would have serious consequence.” Examples of CII are the process control systems that monitor and control electrical power generation, a Global Navigation Satellite System (for example, BeiDou, Galileo, GLONASS, GPS), the information services between banks to settle accounts, and access infrastructure to reach and use global internet services.
Critical Information Infrastructure Protection (CIIP) is a derivative of this CII definition and is defined as: “All activities aimed at ensuring the functionality, continuity, and integrity of CII in order to deter, mitigate and neutralize a threat, risk or vulnerability or minimize the impact of an incident.”
Sometimes the concept of CII may give the false impression that CIIP is a separate area from CIP. While CIP comprises all critical sectors of a nation’s infrastructure, CIIP is only a subset of a comprehensive protection effort, as it focuses on measures to secure critical information infrastructure (Brunner and Suter 2008). For instance, Canada (Canadian National Strategy for Critical Infrastructure),[11] the Czech Republic (Act on Cybersecurity of 2014),[12] and other countries expressly recognize this direct connection between CIP and CIIP within their policy and legal frameworks. Although some countries, such as Serbia, have established separate legal frameworks for both CIP and CIIP, the reality is that both CI and CII can only be adequately protected if they are seen as a single block – while maintaining the technical and regulatory differences (see figure 4).
Figure 4. Relationship between CIP, CIIP, and cybersecurity.
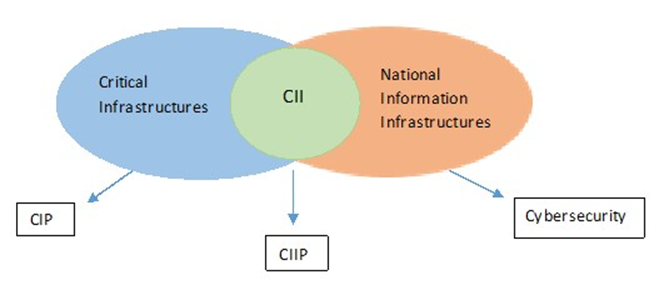
Source: Burnett 2016.
Essential services and critical activities
Although the multiple approaches in the CI/CII definitions should not distract from the need for CIIP, it is important to understand the different CI/CII terminologies and approaches adopted by different international and regional organizations, such as the European Union (EU) and the African Union and by individual countries. For instance, the EU’s Network and Information Security Directive (NIS Directive), currently under review, does not use the term CI. Instead, it uses the economy-driven term “Essential Services.” The directive also defines “Operators of Essential Services” as a public or private entity within the energy, transport, banking, financial market infrastructure, health, drinking water supply and distribution, and digital infrastructure sectors, which meet the criteria laid down in Article 5(2).[13]
In 2008, the OECD adopted a series of Recommendations on the Protection of Critical Information Infrastructures (CIIP Recommendations), which set out a high-level framework to guide the development of national strategies to protect CII domestically and across borders. In 2015, the OECD adopted the 2015 Security Risk Recommendation, in which the OECD adopted a new approach concerning the concept of digital security, which has evolved from the security of technical assets (for example, information systems and networks) to the security of the economic and social activities that rely on them (for example, delivery of energy or emergency health services). In short, the OECD replaced the concept of “cybersecurity” with the term “digital security” because the latter has economic and social implications.
In 2016, the OECD revisited its 2008 CIIP Recommendations report, and the group of experts noted that the concept of CII has rarely been used to develop domestic policy frameworks and that this issue may be because of the difficulty in delineating CII in practice. In 2019, the OECD adopted a new set of CIIP recommendations and replaced the concept of CII with “Critical Activities.” This shift from CII to Critical Activities ensures consistency with the digital security approach of the 2015 Security Risk Recommendation.[14] To date, there is no record that any OECD country has adopted the concept of “Critical Activities” within its policy and legal frameworks, and only a few countries, including France and Colombia, have adopted the concept of “digital security” in their national digital security strategies and policies.
ICT dependencies
Cross-sector and cross-border ICT dependencies
The risk environment affecting the CI/CII is complex and uncertain. Threats, vulnerabilities, and their consequences have evolved over the past two or three decades. CI sectors have been subject to risks associated with physical threats (for example, accidents or technical failures) and natural disasters (for example, extreme weather). However, they are now exposed to cyber-risks, which stem from the growing integration of ICT systems into CI operations and an adversary focus on exploiting potential vulnerabilities.[15]
Explaining ICT dependencies – and interdependencies – is not an easy task (see figure 5); however, the cyberincident described in box 3 illustrates how the ICT dependencies in other CI sectors and services operate.
Box 3. Cyberincident illustrates ICT dependencies

This type of cyberattack is no longer a theoretical concern. For instance, the cyberattacks on Ukrainian power grids in 2015 and 2016 predicted what could happen in the future. In 2016, the DDoS cyberattacks, targeting systems operated by the Domain Name System (DNS) provider Dyn, resulted in major Internet platforms and services (for example, Airbnb, Amazon, CNN) being offline for some time, affecting their service and end users in the United States, Europe, and other regions. Late in 2020, the New York Times reported the first known death as an indirect consequence of a cyberattack. Cybercriminals struck a hospital in Germany with a ransomware attack which invaded 30 servers and crashed systems forcing the hospital to turn away emergency patients. A woman in a life-threatening condition was sent to a hospital 20 miles away and died from treatment delays.[16]
Figure 5. ICT dependency matrix
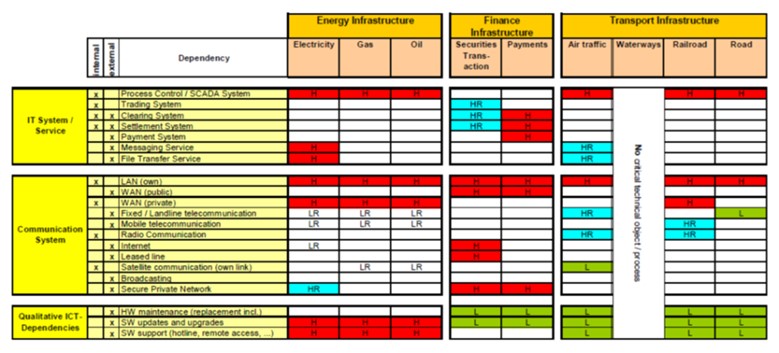
Source: European Commission. 2009. Study on Critical ICT-Dependencies: Energy, Finance and Transport Sectors. https://ec.europa.eu/home-affairs/sites/default/files/e-library/docs/pdf/2009_dependencies_en.pdf.
Figure 6 Interdependencies between different critical infrastructure sectors
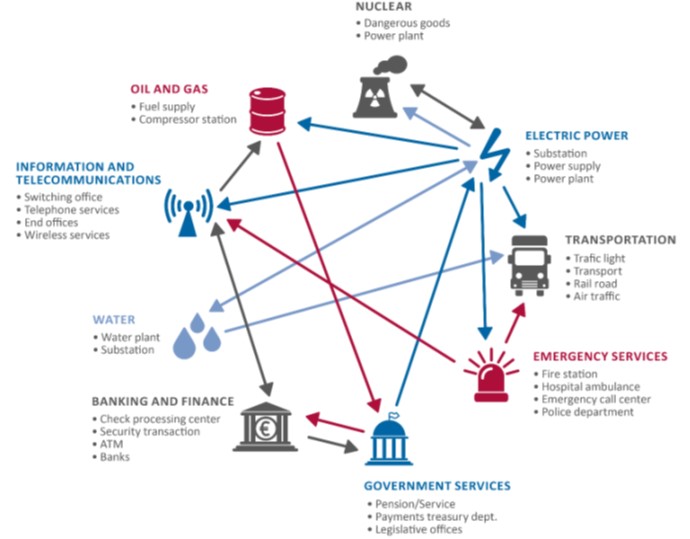
Source: Duane, Petit, and Kim 2017.
Regulatory considerations for protecting the CI/CII operators’ digital transformation
CI/CII operators are not exempt from the digital transformation process. Its adoption improves productivity and efficiency, increases data sharing, enhances flexibility and agility, and gets a return on investment, among other benefits, but one of its main challenges is to minimize the impact of the cyber-related risks and vulnerabilities. The digital transformation process within CI/CII sectors amplifies the complexity, dynamism, and cross-sector and cross-border dependencies and interdependencies of global CI/CII ecosystems, maximizing the potential for systemic and high-impact disruptions. For instance, in May 2017, the Wannacry ransomware attack, which infected more than 200,000 computers across 150 countries, disrupted large companies’ operations, such as FedEx, Nissan Motors, Telefonica, Deutsche Bahn, and National Health Service hospitals in England and Scotland. In June 2017, the NotPetya ransomware attack affected small and multinational companies, such as DHL, Maersk Line, Merck & Co., causing billions of U.S. dollars in damage.
In that context, CI/CII operators should adopt a proactive and risk-management approach. If CI/CII operators understand the current cyberthreat landscape and know how to manage their cyber-related risks, which implies assessing and reducing them to an acceptable level, it increases the probability of economic and social benefits. This risk-management approach cannot eliminate all the risk factors but, if handled effectively, the benefits of digital transformation to CI/CII operations can be accomplished with minimal disruption and cost (OECD 2019).
Since disruptions to CI/CII sectors are regularly in the headlines, it is recommended that key stakeholders of the CI/CII ecosystem work together under a multidisciplinary and collaborative approach to develop and implement national CIP/CIIP policy and regulatory frameworks. These CIIP frameworks should contain, among other things, robust provisions to ensure adequate incident response capabilities, information-sharing mechanisms, cybercrisis management, and preparedness procedures to enhance CI resilience and boost the benefits of digital transformation.
National cybersecurity strategy: policy tool to strengthen the protection and cyber-resilience of CII
Countries may have different motivations to strengthen their national cybersecurity capabilities: (i) initiatives from regional bodies (for example, the African Union, Organization of American States (OAS)), from networks of CII providers (for example, the Commonwealth Telecommunications Organisation), and from international organizations (for example, the World Bank, the International Telecommunication Union (ITU), the North Atlantic Treaty Organization (NATO), and the Organisation for Economic Cooperation and Development (OECD)), which may recommend or even pressure countries to give more attention to national cybersecurity issues, including CIIP (TNO 2017); (ii) as a reactive measure resulting from systematic cyberattacks to national critical services; (iii) as a preventive measure resulting from a national cyber-risk assessment; or (iv) the call from different economic sectors to strengthen national cybersecurity capacities and resilience, among other reasons.
In that context, countries begin national-level discussions (multistakeholder approach), with the support of international partners (for example, ITU, World Bank, African Union, OAS), to identify gaps, national and sectoral cyber-risks, and domestic needs and priorities in the cybersecurity domain. The collected inputs from the public consultation process and the different assessments will feed and shape the content of the national cybersecurity strategy (NCS). The NCS is, in essence, the roadmap that sets out a range of national strategic objectives that should be implemented (and regularly evaluated) in a specific timeframe (see figure 7).
Figure 7. Lifecycle of a national cybersecurity strategy
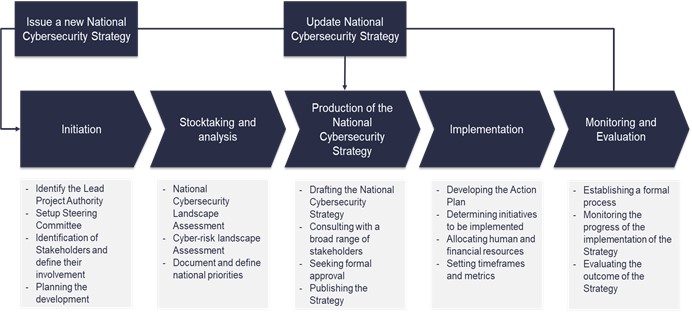
Source: Guide to Developing a National Cybersecurity Strategy.
The first NCS usually addresses multiple CIIP activities, including the identification of the national CI and CII and the development of the CIIP policy and legal framework, as well as other strategic activities, such as the creation of the governance structure and cybersecurity coordination programme (clear roles and responsibilities, budget, resources, action plan), the establishment of the national computer security incident response team (CSIRT), the adoption of cybersecurity education and awareness-raising activities, the adoption of legislative frameworks (for example, cybercrime and data protection laws) and the adoption of domestic and international cooperation mechanisms, among others (see figure 8).
The Guide to Developing a National Cybersecurity Strategy also suggests the following good practices and CIIP-related activities that the NCS should address to ensure the protection of critical infrastructure services and essential services: (i) adopting a risk-management approach (national and sectoral cyber-risk profile), (ii) defining a governance model with clear roles and responsibilities, budget, resources (iii) defining minimum legislative, regulatory baselines and technical requirements, (iv) adopting a wide range of incentives to ensure that the CI/CII operators comply with the minimum technical and legal requirements, and (v) establishing sustainable and formal public-private partnerships and other informal collaboration arrangements.
Figure 8. Focus areas of national cybersecurity strategies
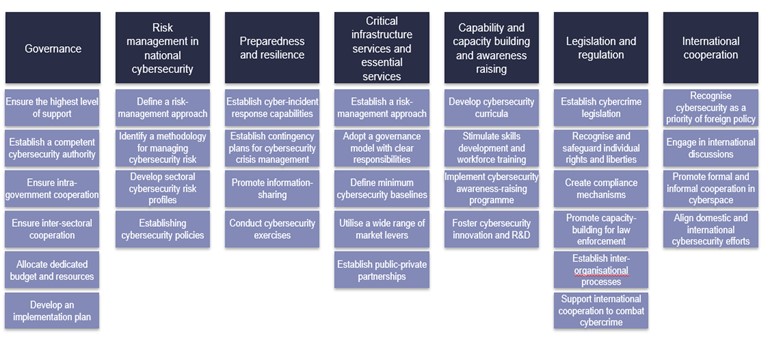
Source: Guide to Developing a National Cybersecurity Strategy.
Identification of national CI and CII sectors
Considering the above best practice and the shared responsibility approach, governments, through coordinating authorities, are responsible for leading and coordinating the CI/CII identification process following the governance and coordination guidelines established in the corresponding NCS. The first step is to identify CI sectors and services and then CII sectors and services – although not all countries have followed that order. Both CI/CII identification processes require the active participation of public and private sector CI/CII operators, among other key stakeholders.
The CI identification process may comprise the following steps:
- To adopt preliminary planning activities to define the scope of the CI identification process, roles, and responsibilities, resources, among other activities.
- To identify the key stakeholders who should be involved in the entire CIP/CIIP process, including the national risk assessment and CI identification consultations. This activity will help define the CIP governance structure and the roles and responsibilities of the key CI stakeholders, including coordinating agencies and the public and private CI stakeholders.
- To determine the country’s risk profile as a whole (for example, national risk assessment) following the different methodologies described below.
- To officially adopt/define the CI sectors through a CIP policy (for example, Canada) or legal framework (for example, Serbia, Montenegro, India). Once identified, it is recommended that the list of national CI sectors and services be broadly disseminated.
As part of this CI identification process, some countries adopt either policy or legal frameworks that set out the identification methodology and other security requirements (for example, Montenegro). Other countries implement risk assessment methodologies provided by international partners (for example, Malawi). As mentioned above, countries also appoint a coordinating body to lead the CI/CII identification process and further CIP activities.
Since the cyberthreat landscape is rapidly changing, it is recommended that the coordinating authorities conduct national (cyber) risk assessments annually to identify new risks and, eventually, new critical services or assets.
A second step is to identify the CII sectors and services. Similar steps, processes, and methodologies can be followed; however, the identification of CII is often more complex than the identification of CI (TNO 2017). Once CI/CII sectors are duly identified, the next step is to identify CII subsectors and services within those CI/CII sectors and the specific CII assets supporting CI services (see figure 9).
Figure 9. CII identification steps (ENISA).
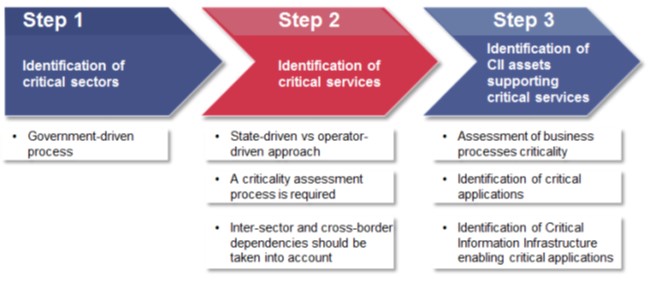
Source: ENISA 2014.
The European Union (EU) adopted Directive 2008/114/EC, which establishes a procedure for identifying and designating European Critical Infrastructures (ECI) in the transport and energy sectors that would have significant cross-border impacts, and also provides a common approach for assessing the need to improve the protection of designated ECI. Also, Montenegro adopted a Law on Designation and Protection of Critical Infrastructures in 2020 to establish the CII identification criteria and requirements following the NIS Directive’s standards. In Malawi, MACRA (the telecommunication regulator), with the support of the Foreign, Commonwealth, and Development Office, conducted a national cyber-risk assessment between 2019 and 2020 to identify its national CI/CII sectors and services. MACRA is currently organizing the 2021 national cyber-risks assessment.
CI/CII key stakeholders
Identifying the key CI/CII stakeholders who should be involved in the entire CIP/CIIP process is vital. There is no exhaustive list of CI/CII stakeholders since each country may adopt a different approach. Several countries have involved public and private sector organizations (for example, CI/CII operators), academia, civil society groups, technical bodies, law enforcement agencies, and international partners, among others (see box 4).
Box 4.Non-exhaustive list of CI and CII stakeholders.

Source: TNO 2017.
National cyber-risk assessment
Effective risk assessment methodologies are the cornerstone of a successful national CIP and CIIP programme. Adopting a risk-management approach is indispensable to identify the current threats, assess vulnerabilities and evaluate their impact on CI and CII assets, systems or networks, considering the probability of the occurrence of these threats (Giannopoulos, Filippini, and Schimmer 2012).
The Guide to Developing a National Cybersecurity Strategy and the GFCE-Meridian report on CIIP (TNO 2017) recommend conducting national (and sectoral) risk profiles to identify the risk of failure of CI and CII sectors and services. The purpose of national and sectoral risk profiles is to establish a common understanding of the risk factors that a country or a specific economic sector faces through systematic assessment of threats and the consequences of the failure of CI and CII. The systematic assessment of threats implies that all threats are assessed based on their impact and likelihood of occurrence using the same set of metrics. The result of this risk assessment is an overview of risk factors and their relative position concerning the impact and frequency of occurrence. Each risk that is addressed in a national/sectoral risk profile may form the basis of an integrated national/sectoral approach to risk prevention, preparedness, and response. Considering the CI and CII related risks in the context of a national/sectoral risk profile may help to develop an integrated and balanced risk-management approach underpinning CIP and CIIP (TNO 2017).
There are different risk assessment focus-areas (Georgios, Filippini, and Schimmer 2012):
- Organizational ICT systems approach (for example, Framework for Improving Critical Infrastructure Cybersecurity from the U.S. National Institute of Standards and Technology (NIST) and the U.K. HMG Technical Risk Assessment IA Standard No. 1);
- Sectoral-level approach (for example, Better Infrastructure Risk and Resilience methodology);
- National-level approach (for example, National Cyber Threat Assessment 2020 – Canada, and the National Cyber Risk Assessment implemented by the U.K. Foreign, Commonwealth and Development Office in multiple Commonwealth countries in Africa and the Caribbean);
- Regional-level approach (for example, EU Risk Management Capability Assessment Guidelines (RMCA) support national authorities to determine their national risk profile. RMCA is a (non-binding) comprehensive and flexible methodology that will set the scene for national authorities to self-assess their risk management capability).
The European Union Agency for Cybersecurity (ENISA) has highlighted two basic approaches to national-level risk assessment (ENISA 2014):
- Centralized risk assessment (or state-driven approach): This is a one-size-fits-all model; the coordinating authority requires identified actors (CI operators) to implement a particular or unified standard for risk assessments. The United Kingdom has implemented this risk management approach.
- Decentralized risk assessment (or operator-driven approach): Each identified actor (CI operator) prepares its own risk assessment to be integrated by a coordinating authority. Nordic countries, Sweden and Denmark, Japan and Switzerland, have implemented decentralized risk assessment approaches.
Different methodologies may also be used:
- The scenario-based approach: Identified actors are gathered to consider scenarios in the round; such scenarios describe risks as a narrative and label them by applying simple categories of likelihood and impact (low, medium, high). The telecommunication sector in Denmark has used this risk assessment approach.
- The qualitative approach: Countries with a specific threat modelling technique in place tend to use qualitative models. Qualitative assessments are the usual approach used by countries when deciding upon the significance of a threat. Qualitative models with a broad range of threats are common in the Nordic countries.
- The quantitative approach: This specific approach applies ordinal thresholds (for example, specific risks are classified as severe if it affects 200 in 20,000 or outages for five days or more). Japan has implemented this approach.
- The hybrid approach: combines all the above elements (for example, using scenarios and then qualitative and quantitative methods). The Netherlands has implemented this model.
CIIP policy and legal frameworks
The foundation of the CIP/CIIP policy and legal frameworks are: (i) government leadership and commitment, which establishes effective coordination between government and public and private CI/CII operators, and (ii) a shared responsibility approach, in which government and public and private CI/CII operators are jointly responsible for the protection of the CI/CII sectors and assets. In that context, the government is responsible for ensuring the continuity of critical sectors and services, and the CI/CII operators are responsible for the security of their infrastructure needed to deliver the critical service.
Countries should at least develop and adopt a basic CIIP regulatory framework comprising the following activities:
- identification and regular re-appraisal of CII sectors and services;
- appointment of a coordinating agency with clear legal mandate and roles and responsibilities, and sufficient resources to operate as such;
- security requirements and legal obligations, such as regular risk management assessments and auditing mechanisms, vulnerability disclosure and information-sharing mechanisms, incident reporting obligations, security requirements for CI/CII supply chain, among others;
- sustainable public-private partnerships;
- cooperation mechanisms with regulatory bodies, government agencies, and international partners; and,
- public awareness-raising campaigns, among others.
If there is no national cybersecurity incident response team (CSIRT) in place, coordinating authorities should consider establishing a national CSIRT with clear instructions to support the CI and CII ecosystems, or at least seek technical support from other domestic incident response teams (for example, military/defence CSIRT), while the national CSIRT is established.
Models of CIIP regulatory frameworks
Commonly, countries change their CIIP regulatory posture to keep pace in the fast-changing environment – such as the United States, which initially adopted a hands-off approach and then opted for a self-regulation approach. Coordinating authorities may consider a broad range of policy and legal options to ensure that domestic CII sectors and services are adequately protected. The adoption of any policy and legal option depends on multiple factors, such as domestic needs and priorities, the cybersecurity maturity level of the country at large and CI/CII ecosystem, the type of threats that they are facing, the type of stakeholders involved in the CIIP, the domestic compliance culture, and the government’s posture, among others.
Government intervention and regulatory continuum are the two main components that will determine the CIIP regulatory framework options. From a theoretical perspective, the GFCE-Meridian report on CIIP (TNO 2017) and other organizations and researchers (Assaf 2008) suggest that the CIIP regulatory framework choices include (see figure 10):
- Market mechanisms and incentives (also known as hands-off approach).
- Self-regulation, which comprises two subcategories: voluntary self-regulation and enforced self-regulation.
- Legal and regulatory framework, which comprises two subcategories: command and control regulation, and mandatory government programme.
- Government ownership.
Figure 10. Models of CIIP regulatory frameworks.
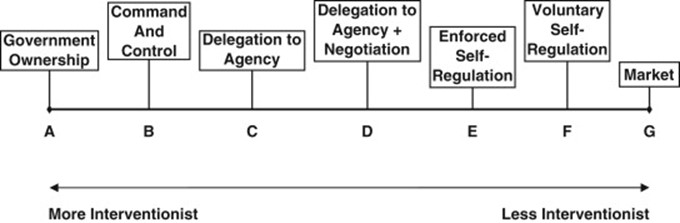
Source: https://www.researchgate.net/figure/Regulatory-continuum_fig1_234050880.
CIP/CIIP governance and regulatory frameworks
Examples of selected CIP/CIIP national governance and regulatory frameworks are shown in tables 2-6.
Table 2. CIP/CIIP governance and regulatory frameworks in Australia[17]
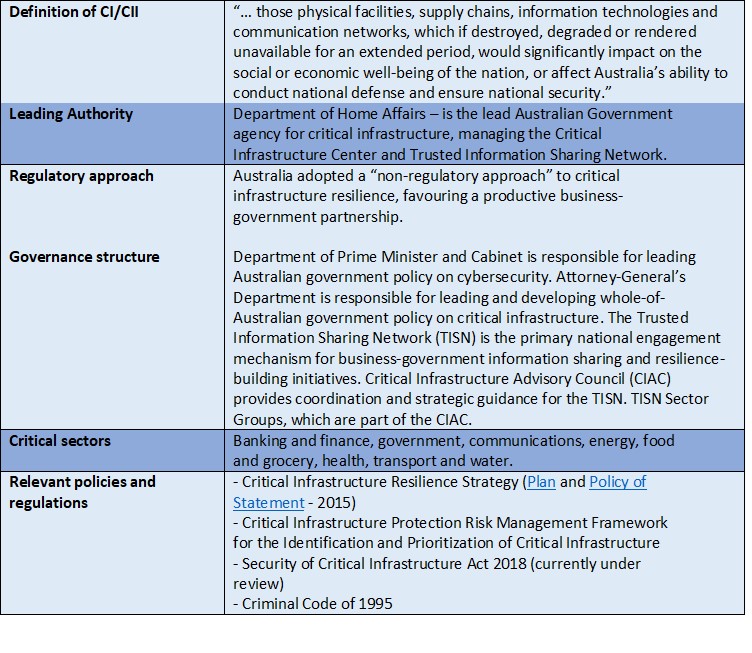
Source: Australian Government. Department Home Affairs. Protecting Critical Infrastructure and Systems of National Significance. https://www.homeaffairs.gov.au/reports-and-publications/submissions-and-discussion-papers/protecting-critical-infrastructure-systems.
Table 3. CIP/CIIP governance and regulatory frameworks in Brazil
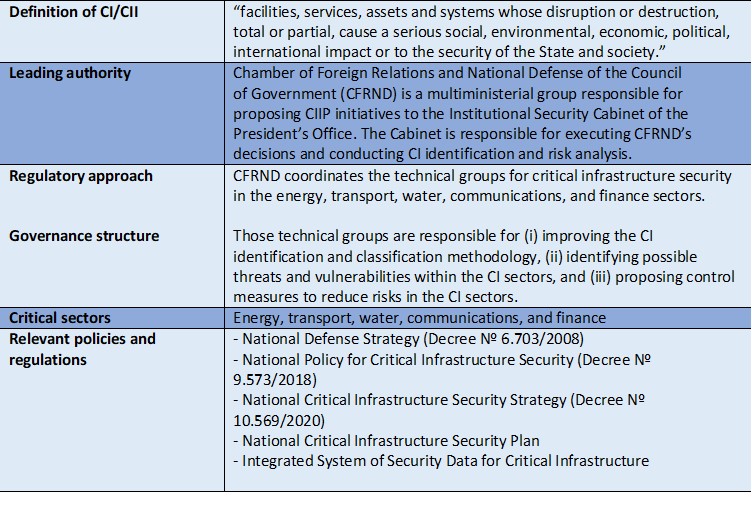
Source: Interview with Barbara Marchiori de Assis, February 18, 2021.
Table 4. CIP/CIIP governance and regulatory frameworks in the European Union
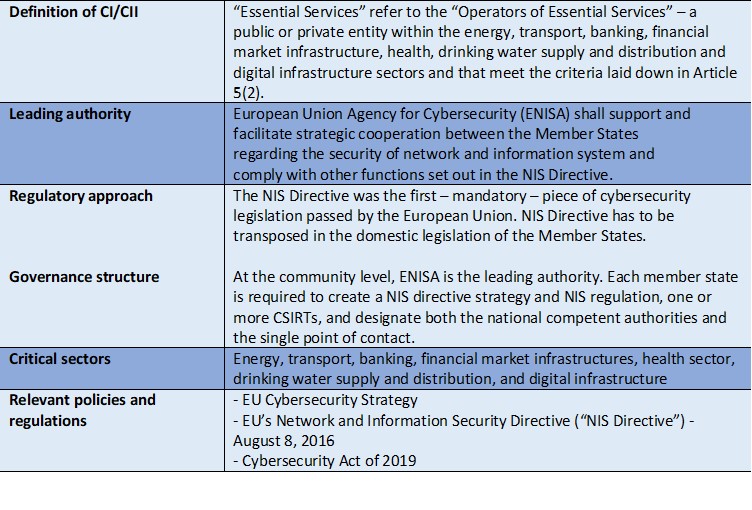
Source: https://ec.europa.eu/jrc/en/research-topic/critical-infrastructure-protection.
Table 5. CIP/CIIP governance and regulatory frameworks in Serbia
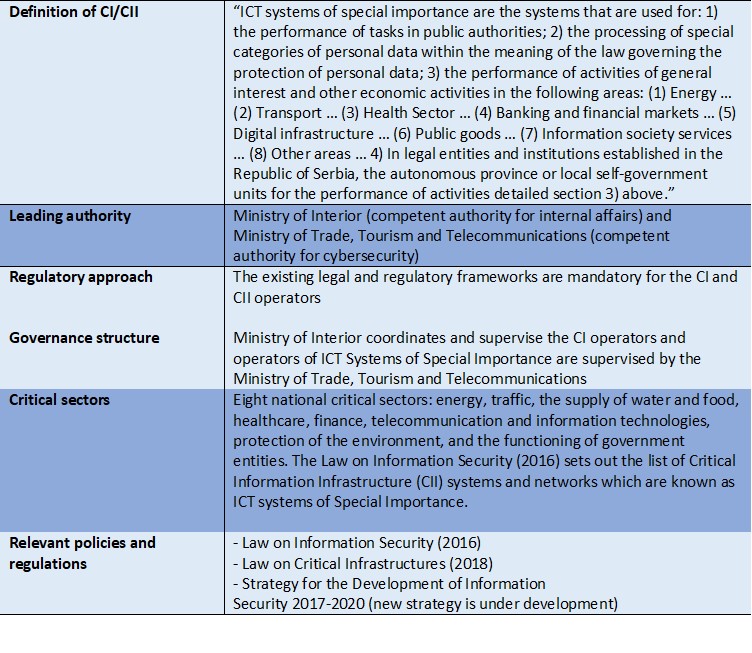
Source: Interview with Natalija Radoja, February 19, 2021.
Table 6. CIP/CIIP governance and regulatory frameworks in the United States
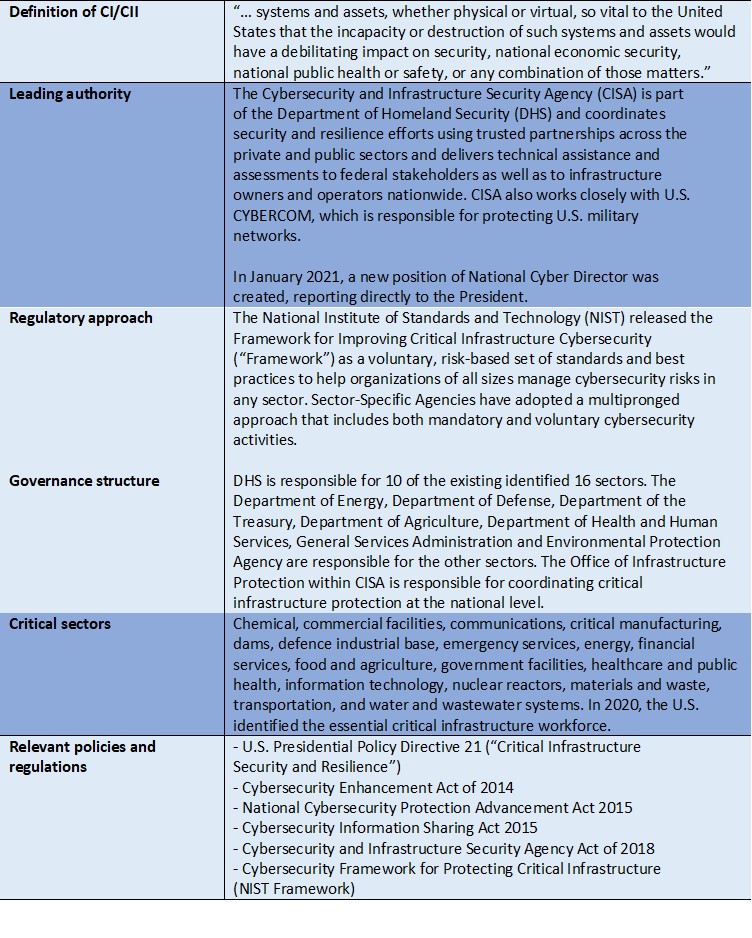
Source: Interview with Paul Rosenzweig, February 25, 2021.
National/sectoral CIIP coordinators
The ITU ICT regulatory database shows that 89 out of 195 countries worldwide have adopted CIIP programmes and regulatory frameworks. In 51 countries, the ICT regulator is responsible for CIIP, being mainly in Africa and Europe, where ICT regulators have an active role in protecting CII.[18] Those statistics also reveal that there are 38 countries with CIIP programmes and regulatory frameworks in place; however, the national CIIP coordinating role is played by other government agencies (see figure 11). Also, 106 out of 195 countries do not have any CIIP programmes or regulatory frameworks, which is still significant considering the current cyberthreat landscape and the importance of protecting the CII sectors and services.
Figure 11. National and sectoral CIIP coordinator’s profile
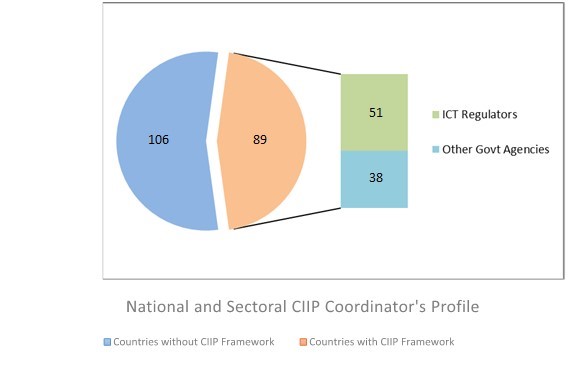
The above statistics also show that there are at least two main CIIP coordinator’s profiles: ICT regulators and other government agencies (for example, independent government agency or government ministry). Although countries may adopt different approaches in this regard, national or sectoral CIIP coordination may fall within the mandate of the following entities:
- The ICT regulator (for example, MACRA in Malawi and the Telecommunications Regulatory Authority in the United Arab Emirates – national-level CIIP coordinator. The Finnish Communications Regulatory Authority and the Swedish Post and Telecom Authority are the primary government agencies responsible for CIIP within the communications sector – sectoral-level CIIP coordinator).
- An independent government agency, centre or committee, for example, National Centre for Critical Infrastructure Protection in Spain (CIP/CIIP), the Cybersecurity and Infrastructure Security Agency in the United States (CIP/CIIP), the Committee for the Protection of Information Infrastructure in the Republic of Korea (CIIP), the Information Security Agency (CIIP) in Estonia, the National Critical Information Infrastructure Protection Centre in India, and the National Agency for the Security of the Information Systems (CIIP) in France,
- A government ministry, such as the ministry of interior or internal affairs (CIIP) or ICT ministry (CIIP). In Serbia, the ministry of interior deals with CIP, while the ICT ministry is responsible for CIIP, or
- A computer security incident response team, for example, the Information Technology Security Incident Response Institution (CERT.LV) is responsible for the routine daily operation of the CIIP in Latvia.
In some countries, the national CIIP coordination role is played by one or multiple government authorities. For instance, the national CSIRT and the National Security Agency are jointly responsible for protecting the CIIP sectors and services in the Czech Republic. In France, ANSSI is the principal government agency dealing with CIIP. At the ministerial level, the ministry of interior (for example, Germany, Hungary) or the ministry of defence (for example, Denmark, Latvia) are usually involved in CIIP activities – mainly in European and African countries.
When there is a defined CIIP policy and regulatory framework, the national CIIP coordinator will have specific legal mandates, functions, and responsibilities to interact with the CII community. The national CIIP coordinator’s legal mandate may be broad – national level (for example, Malawi) – or limited – sectoral level (for example, Finland) and should have sufficient technological, financial, and human resources to operate as such. The CIIP coordinator must ensure that the CII operators comply with the CIIP policy and regulatory frameworks, including the security requirements and legal obligations detailed in the following sections as minimum standards. The national CIIP coordinator should also develop and promote domestic and international cooperation arrangements among the key CII’s stakeholders and international partners.
As noted above, the great majority of the countries do not have a CIIP regulatory framework in place. For instance, in the African region, out of 44 surveyed countries, 19 countries have an NCS in place which comprise both CIIP and resiliency plans. In the Americas region, out of 35 surveyed countries, only 13 have an NCS in place containing both CIIP and resiliency plans, only four countries address resiliency plans, and 18 do not have an NCS in place. In the Arab region, at least 11 countries have developed an NCS covering both CIIP and resiliency plans, only two countries address resiliency plans but no CIIP regulations, while nine do not have an NCS in place. In the Asia-Pacific region, 17 countries have an NCS in place covering both CIIP and resiliency plans, only three countries address resiliency plans, and 18 do not have an NCS. In the Commonwealth of Independent States, only one country has an NCS in place addressing both CIIP and a resiliency plan, three countries address resiliency plans but no CIIP regulations, and five do not have an NCS in place. Last, in the European region, 37 out of 46 countries have developed an NCS which contains both CIIP and resiliency plans, only three countries address resiliency plans, and six do not have NCS in place (ITU 2021) (see figure 12).
Figure 12. Countries with an NCS addressing CIIP and cyber-resiliency plans by region
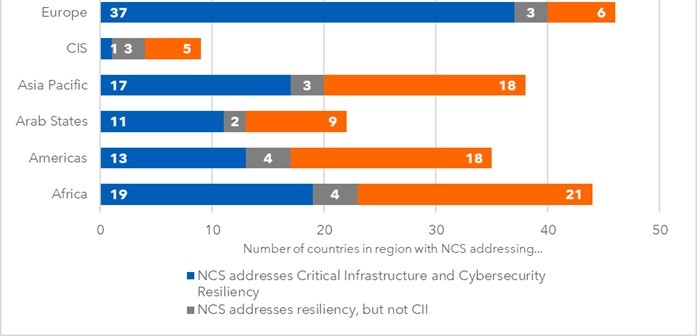
Source: ITU 2021.
In that context, should the sectoral regulators, including ICT regulators, adopt a proactive cybersecurity posture to ensure that the CI/CII sectors and services are adequately protected? If competent authorities, including ICT regulators, are not taking any action, the national CII sectors and services are not secure; and therefore, CII, and other CI sectors, are highly exposed to cyber-risks and vulnerabilities.
In those countries, it is recommended that at least the ICT regulators adopt a proactive cybersecurity posture and find the appropriate legal way to oblige CII operators to meet some baseline security requirements (for example, regular cyber-risk assessments and internationally recognized standards) and legal obligations (for example, incident reporting) to ensure that CII is secure. ICT regulators typically do not have the resources and capacity to provide technical support (for example, incident response management) when cyberincidents occur unless there is a sectoral CSIRT (for example, COMM-CSIRT Botswana,[19] NCSC-FI in Finland). ICT regulators should consider establishing formal communication channels to exchange information with the CII operators and other relevant actors in times of crisis. ICT regulators should also consider establishing communication and collaboration mechanisms with the national CSIRT, domestic or sectoral CSIRTs, law enforcement agencies, and international partners. Although CII operators are typically diligent, especially multinational companies, requiring those minimum security requirements and legal obligations will help CII operators to detect and mitigate the negative impact of cyberincidents while competent authorities develop any CIIP programme, governance structure, and policy and legal frameworks.
CIP/CIIP: security requirements and legal obligations
Within the broad CI/CII regulatory framework spectrum, there are some standard minimum security requirements and legal obligations that the CI/CII operators and owners in different countries must meet to ensure that the CI/CII sectors and services are adequately protected.
Security standards[20] and certification schemes
The goal of security standards is to improve the security of information technology systems, networks, and critical infrastructure. Governments and businesses are implementing security standards either because (i) they are mandatory in some countries or (ii) as good practice, under a voluntary self-regulation scheme. Numerous security standards have been developed to help organizations manage security risks and implement security controls that meet legal and regulatory requirements and achieve performance and cost benefits.
Some security standards are developed by countries, such as the U.S. NIST Cybersecurity Framework, or by international organizations, such as the International Organization for Standardization (ISO), the North American Electric Reliability Corporation (NERC), and the European Telecommunications Standards Institute (ETSI). ISO has developed several widely used security standards, such as ISO/IEC 27032 (guidelines for cybersecurity), ISO/IEC 27001 (information security management systems), ISO 22301 (business continuity management systems), ISO/IEC 15408 (evaluation criteria for IT security), ISO/IEC 27035 (information security incident management), ISO/IEC 27005 (information security risk management).
There are also security standards that have been developed for specific CI sectors, such as the NERC-CIP, which is a set of standards that specifies the minimum-security requirements for bulk power systems; NIST 800-13, which contains some security guidelines for the telecommunications management network; and ETSI GR IP6 008 V1.1.1 (2017-06), which is focused on IPv6-based Internet of Things deployment.
There is also a global need to develop and implement cybersecurity certification frameworks to ensure and maintain the highest security standards and trust in ICT products, services, and processes, including CII networks and systems. Currently, there is a patchwork of cybersecurity certification schemes and initiatives worldwide; however, countries do not mutually recognize them. EU countries are developing mutually recognized certification schemes. The EU Cybersecurity Certification Framework (CCF) has been adopted following the provisions of the NIS Directive and Regulation 2019/881 (known as the Cybersecurity Act). ENISA is currently defining different certification schemes covering ICT products, services, and processes,[21] such as cloud and 5G services.
Risk management
Identifying, managing, and evaluating the existing risks will enhance the resilience of CI/CII sector assets. Many countries have developed risk management policies and guidelines (for example, Cyber Risk Assessment Guidelines developed by the Singapore Cyber Security Agency (CSA 2019)) based on the ISO 31.000 standard, which applies to CI/CII operators. For instance, the NIS Directive promotes a risk management culture, which involves implementing risk assessments and security standards and measures to mitigate identified risks. This risk management culture is developed through appropriate regulatory requirements and voluntary industry good practices. For instance, the Serbian Law on Information Security states that CII operators have to observe some guiding principles, including the risk management principle, when planning and implementing security and protection measures. Also, the Spanish Law on Critical Infrastructure Protection (Law No. 8/2011) requires sectoral risk analysis in the identified CI sectors.
In other CIP/CIIP regulatory frameworks, risk assessments focus on relevant supply chain risks, such as the new NERC Reliability Standard CIP-013-1, which deals with the supply chain risk for industrial control system hardware and software and computing and networking services associated with Bulk Electric System operations (NERC 2020).
Cyberincident reporting obligation
Many countries have established incident reporting obligations to the CI/CII operators (for instance, the EU NIS Directive, the U.K. Network and Information System Regulations 2018, NERC mandatory reporting, and the Australian Security of Critical Infrastructure Act of 2018 (currently under review). CI/CII operators are obliged to report significant cyberincidents, which meet specific requirements, to the CI/CII regulator and/or the national CSIRT. Prompt and detailed reporting can lead to early detection and prevent incidents against other CI/CII sectors. Some cyberincidents must be reported within a timeline upon discovery. For instance, US-CERT Federal Incident Notification Guidelines establishes that the cyberincident must be reported within one hour of being identified. The NIS Directive states that a cyberincident has to be reported without undue delay. The following criteria will determine whether or not the cyberincident should be reported: (i) number of users affected by the disruption of the services, (ii) the duration of the incident, and (iii) the geographical spread concerning the area affected by the incident. The regulatory framework of other countries may have different criteria and requirements.
In the United Kingdom, competent authorities are designated on a sectoral basis, so they outline their own incident reporting threshold and requirements. Also, the EU General Data Protection Regulation (GDPR) establishes that an incident (for example, data breach) has to be reported within the next seventy-two hours from discovery; this timeline may apply to the CI/CII operators (for example, healthcare sector) if the subject incident is within the GDPR’s scope.
It is important that the CIIP coordinator, including the CI/CII regulators, and the national CSIRT establish coordinated mechanisms to receive incident reports, such as an online reporting platform, freephone number, email address, or any other physical or electronic means, including walk-in reporting. Some countries have established coordinated incident reporting portals in which the details of the cyberincident can be shared in real time with the national CSIRT, law enforcement agencies, and other relevant stakeholders (for example, Serbia and Australia).
Information-sharing mechanisms
Information sharing is the most important element in each stage of the CIIP process. It provides a better understanding of threats, risks, and dependencies, expediting response through knowledge sharing of possible countermeasures. Bidirectional information sharing is highly recommended. Both public and private CII operators need to be involved, and information needs to circulate in both directions. In that context, information sharing is considered a public-private partnership (PPP) activity (Garcia Zaballos and Jeun 2016).
Several countries have developed coordinated information-sharing groups or networks in the CIIP arena, such as the Trusted Information Sharing Network in Australia, and information sharing guidelines, such as the U.S. Critical Infrastructure Threat Information Sharing Framework. The Canadian authorities created an online information-sharing platform, called the Critical Infrastructure Gateway, to exchange information with other relevant stakeholders. This platform hosts information, including risk management documents, best practices, lessons learned, standards, among others. This information-sharing platform requires a membership, which is granted only to stakeholders belonging to a CI sector network and to relevant government partners (Garcia Zaballos and Jeun 2016).
The NIS Directive states that information sharing shall be limited to what is relevant and proportionate to the purpose of such exchange and shall preserve the confidentiality of that information and protect the security and commercial interest of essential services and digital services.
Many information-sharing activities and resources have been implemented utilizing multiple protocols and guidelines designed to preserve the confidentiality of the information and build trust among the different members of the community. For instance, the Traffic Light Protocol Framework employs four colours to indicate expected sharing boundaries to be applied by the recipients. In some environments, the Chatham House Rule is also used to protect information sources.[22]
These are some recommendations for CI/CII operators which have not started exchanging information: (i) “Share early and share often,” but it is essential in times of crisis, (ii) identify information sharing venues before a crisis, (iii) identify all actors’ information requirements and priorities, (iv) create incentives to share information, and (v) establish redundant communications (INSA 2018).
Supply chain security
Supply chains are currently facing a broad range of threats, from physical threats to cyberthreats, so that supply chain management and security are becoming increasingly important in the energy, telecommunications, defence, and other CI sectors. Many companies, including CI/CII operators, are becoming more dependant than ever before on third parties’ products, such as software, hardware, and services, such as cloud-based technologies. However, CI/CII operators cannot always control which security measures their supply chain partners implement, making them vulnerable to potential supply chain breaches. For instance, see the SolarWinds attack, the AIRBUS attack and the Covid-19 Vaccine attack.
Despite the above, most countries are not establishing robust supply chain security requirements within the CIP/CIIP regulatory frameworks. Implementing supply chain security standards (for example, ISO 28.000 Security Mgmt. Systems for the Supply Chain, and NERC CIP-013-1 Cyber Security – Supply Chain Risk Mgmt.), good practices (for example, security by design/by default), and solid supply chain contracts, is insufficient to adequately protect CI/CII sectors and services from supply chain cyberattacks.
For instance, the NIS Directive does not impose any specific supply chain security requirements. However, Operators of Essential Service (OES) or Digital Service Providers (DSP), who rely on third-party vendors’ products and services, are responsible for protecting any essential service. This means that there should be confidence that all relevant security requirements are met regardless of whether the ORS/DSP or a third party delivers the service (DCMS 2018). Owing to this situation, the NIS2 (draft of the revised NIS Directive) proposes to address the security of the supply chain and suppliers’ relationships by requiring individual companies to address cybersecurity risks in supply chains and suppliers’ relationships. The proposed changes also aim to strengthen the supply chain security for key ICT technologies at the European level.[23] Indeed, the NIS2 will change the supply chain security requirements and standards within the EU.
Given the above situation, in the United Kingdom, both the National Cyber Security Centre and the Centre for Protection of National Infrastructures proposed 12 principles designed to help companies, including CI/CII operators, establish effective control and oversight of their supply chain.
In 2020, Singapore adopted a CII Supply Chain Program, as a national effort, to establish processes and good practices to help CII operators and their vendors manage supply chain risks holistically and strengthen their overall supply chain cybersecurity posture. This programme will be guided by three key principles: assurance, transparency, and accountability.[24]
In 2019, the U.S. President issued an Executive Order on Securing the Information and Communications Technology and Services Supply Chain (EO 13873) to strengthen efforts to prevent foreign adversaries from exploiting vulnerabilities in the ICT supply chain and protect the vast amount of sensitive information being stored in and communicated through ICT products and services. Also, the Cybersecurity and Infrastructure Security Agency (CISA), through the National Risk Management Center, is committed to working with the government and industry partners to ensure that supply chain risk management (SCRM) is an integrated component of security and resilience planning for the nation’s infrastructure.
Regarding specific SCRM security standards within CI’s sectors, the U.S. Federal Energy Regulatory Commission (FERC) released three new CIP standards that address supply chain risk management for bulk electric systems operations. The North American Electric Reliability Corporation (NERC) developed these standards to address the risks associated with the supply chain for grid-related cybersystems (Skeath 2018). Also, NIST 8276 Key Practices in Cyber Supply Chain Risk Management has a multidisciplinary approach to manage cybersecurity risks associated with their supply chains. NIST 8276 standards can be implemented by any company of any size, scope, and complexity, including CI/CII operators (Boyens and others 2021).
Coordinated vulnerability disclosure
Vulnerability disclosure is a process through which vendors and vulnerability finders may work cooperatively in finding solutions that reduce the risks associated with a vulnerability (ISO/IEC 29147). Coordinated vulnerability disclosure practices have proved to be of great importance for public and private CI/CII operators.
In some countries, the establishment of vulnerability disclosure policies and guidelines is mandatory for public sector agencies, such as the U.S. federal civilian agencies, which since March 2021, has been obliged to develop their own vulnerability disclosure policy. These policies create the pathway for ethical hackers, researchers, software developers, and security professionals to submit and communicate relevant information about potential threats and vulnerabilities.
In India, the National Critical Information Infrastructure Centre runs a Responsible Vulnerability Disclosure Program to report any vulnerability in the CII environment, which may cause severe damage to the ICT infrastructure or processed information.[25] In France, the National Agency for the Security of Information Systems (ANSSI) has implemented a coordinated vulnerability disclosure policy.
Incident response management
ENISA defines incident response management as “… the protection of an organization’s information by developing and implementing an incident response process (for example, plans, defined roles, training, communications, management oversight) in order to quickly discover an [cyber] attack and then effectively contain the damage, eradicate the attacker’s presence, and restore the integrity of the network and systems” (ENISA 2019). The NIS Directive instructs Member States to create one or more CSIRTs for the CI/CII sectors to support them in the risk management and incident handling process.
Some CI/CII operators have developed coordinated incident response capabilities at the organizational level, either through well-equipped computer security incident response teams (CSIRT) or Security Operation Centres (SOC). Other CI/CII operators obtain incident response support either from regional headquarters – widespread in the telecommunication and banking sectors – or domestic or regional security service providers.
Some countries have established sectoral CSIRTs that serve CI/CII operators within a specific sector (for example, COMM-CSIRT in Botswana). There are also national CSIRTs (for example, US-CERT in the United States, SRB-CERT in Serbia, CERT-MU in Mauritius) which provide incident response support not only to the public and private sector organizations at large but also to the CI and CII community. In some countries, the military/defence CSIRTs have a specific mandate to monitor and protect CI/CII sectors.
Considering the current cyberthreat landscape, both government and CI/CII operators have to work closely in this particular area to ensure that the CI/CII operators have coordinated incident response capabilities and an internal incident response plan to ensure the continuity of the operation (cyber-resilience). Some countries have developed national incident response plans (for example, the U.S. National Incident Response Plan)[26] to articulate the roles and responsibilities, capabilities, and coordinating structures that support how the country responds to and recovers from significant cyberincidents posing risks to CI’s sectors and services.
Cybercrisis management
Countries like Estonia and Ukraine have faced real cybercrises. The concept of cybercrisis management is still under development; not all countries have integrated cybersecurity within their general crisis management structures and policy and legal frameworks.
National-level risk analysis on CI/CII sectors and services is essential to the development of national cybercrisis contingency plans, which require a multiple-stakeholder and multisector approach where government, private sector organizations, academia, and civil society work together to develop and implement cooperation arrangements for addressing incidents or crisis in the cyberdomain. For instance, in Malaysia, the National Cyber Security Agency is the custodian of the National Cyber Crisis Management Plan, which provides specific guidelines and procedures to manage and coordinate national cybercrises caused by major cyberattacks against critical national information infrastructure.[27]
Early warning networks and national cyberexercises (for example, U.S. Cyber Storm is a large-scale, national-level exercise involving the private and public sectors) are two vital actions that the CI/CII community should consider implementing to enhance the resilience of the CI/CII sectors and services. In Singapore, the Cybersecurity Act of 2018 compels CII owners to participate in cybersecurity exercises to test the state of readiness of CII owners to respond to significant cybersecurity incidents.
Even though some countries, such as the United States, and international organizations, such as NATO and the ITU, regularly organize cybersimulations for government officials, the reality is that not many countries are conducting regular cyberdrills at the national level. Some countries have identified that more resources, better planning, and the participation of key stakeholders from the government, private sector, academic, civil society, among others, are required to conduct a national cyberdrill at least once a year,.
Monitoring and sanction mechanisms
Most of the existing CIP/CIIP regulatory frameworks have established monitoring mechanisms (for example, regular compliance reports) and sanctions (for example, monetary fines) to ensure that CI/CII operators comply with the security requirements and legal obligations. For instance, the NIS Directive instructs Member States to implement and enforce those mechanisms, including ex-ante and ex-post supervision depending on the CI sectors and services. For example, the Serbian Law on Information Security establishes monetary fines for those CII operators who break the law.
According to the NIS Directive, Member States are required to set their own rules on monetary penalties and take measures to ensure that the operators of essential services and digital services providers comply with the directive and domestic NIS regulations. For instance, in the United Kingdom, non-compliant organizations may be fined up to GBP17 million (Part 5 of the NIS Regulations).[28] The relevant competent authority will assess the level and severity of the fines. In Singapore, the Cybersecurity Act of 2018 sets out several penalties for non-compliant CII owners, ranging from being liable for fines (not exceeding $100,000) or imprisonment (not exceeding two years) or both.[29]
Domestic and international cooperation mechanisms
Cooperation initiatives between government and CI/CII operators
In many countries, the private sector owns and operates a great majority of the national CI/CII services (for example, more than 80 per cent in the United States). Moreover, private sector CI/CII operators are at the forefront of investment and efforts to develop new production and protection technologies. This, combined with the fact that the primary responsibility for protecting CI/CII services lies with CI/CII operators and owners, highlights the importance of establishing informal and formal collaboration arrangements between governments and public and private CI/CII operators to achieve adequate levels of resilience. The benefits of mutual support, resource pooling, and joint decision-making between the government and public and private CI/CII operators could be extended to areas of common interest, such as security and risk assessments, review of security measures, CI/CII asset identification, development of cybercontingency plans, incidence response management and training (UNOCT 2018). Creating information-sharing mechanisms is crucial to incentivize public-private collaboration arrangements. This collaborative and trusted environment is essential to ensure CI/CII security and resilience (see boxes 5 and 6).
Box 5. Petnica Group: public-private partnership in Serbia

Source: World Bank. 2019. Cybersecurity Capacity Review in Serbia. https://gcscc.ox.ac.uk/files/cmmserbiafinalreportpdf; Rizmal, Irina. 2018. “The ‘Petnica Group:’ A case of Public-Private Partnership for Cyber Security in the Republic of Serbia.” In Michael Bartsch and Stefanie Frey (eds). Cybersecurity Best Practices. https://link.springer.com/chapter/10.1007/978-3-658-21655-9_9
Box 6. Canadian Forum for Digital Infrastructure Resilience (CFDIR): public-private partnership in Canada

Source: Government of Canada. Canadian Forum for Digital Infrastructure Resilience. https://www.ic.gc.ca/eic/site/smt-gst.nsf/eng/sf11618.html.
Collaboration initiatives between national CSIRTs and CI/CII operators
CIP/CIIP regulatory frameworks typically set out collaboration channels with multiple government agencies, including national CSIRTs. These technical bodies play an important role in the CIP/CIIP process and conduct relevant activities, such as: (i) identifying, monitoring, and recording national-level cyberincidents, including those affecting CI/CII sectors and services; (ii) providing early warning to the CI/CII community about cyberthreats, (iii) providing training and awareness-raising campaigns; and (iv) acting as a national or sectoral point of contact for collaboration and information sharing activities (for example, incident reporting, vulnerability disclosure) with other public and private sector CSIRTs (for example, government and military CSIRTs), national, regional and international CSIRTs (for example, African CERT, Americas CSIRT) and incident response forums and organizations (for example, FIRST.org). However, its core function is to provide technical support to CI/CII operators in their incident response management cycle. For instance, the UK-CERT, Q-CERT (Qatar), and many other national CSIRTs are responsible for providing incident management support to CI/CII operators.
The national CSIRTs also participate in defining the scope of CIP/CIIP, identification of CI/CII sectors and services, development and implementation of risk management and cybercrisis management plans, and other security guidelines for CIP/CIIP (ENISA n.d.). The national CSIRTs also register and record all cyberincidents against CI/CII sectors and deploy awareness-raising campaigns. A coordinated channel of collaboration and communication between national CSIRTs and CI/CII operators is critical to respond to cyberincidents when they occur or during times of crisis. In some countries, military CSIRTs and certain sectoral CSIRTs are instructed to monitor and protect CI/CII assets during times of crisis.
Collaboration initiatives between domestic and international law enforcement agencies and CI/CII operators
Strengthening resilience of CI/CII sectors requires collaborative work from different partners and key stakeholders within the CI/CII ecosystem, including domestic and international law enforcement agencies.
When there is suspicious activity, an imminent cyberthreat or a confirmed cyberattack to a specific CI/CII sector, service or facility, CI/CII operators are obliged to report the incident to domestic law enforcement agencies. However, when there is evidence that they are dealing with a cross-border attack (for example, Wannacry, NotPetya), international law enforcement agencies (for example, the International Criminal Police Organization (INTERPOL), the European Union Agency for Law Enforcement Cooperation (Europol)) should also be notified.
At the national level, law enforcement agencies, particularly with the cybercrime investigation units, will provide technical support in digital forensics to investigate and collect relevant digital evidence associated with the cyber-attacks on CI/CII. Many countries have enacted substantive cybercrime provisions that criminalize cybercrime-related offences, including illegal activities intended to block, harm, and destruct CI/CII sectors and services.
INTERPOL, Europol, and other law enforcement agencies are highly active in supporting countries and businesses which are victims of cyberattack on CI/CII sectors and services. A recent INTERPOL report revealed a significant target shift from individuals and small businesses to major corporations, governments, and critical infrastructures (INTERPOL 2020). This report contains several recommendations, such as sharing timely information, enhancing police collaboration and cooperation among member countries, using INTERPOL’s Cybercrime Collaborative Platform, implementing prevention measures and raising awareness, enhancing cybercrime investigative capabilities (Virtual Global Academy), and strengthening public-private partnerships. Establishing coordinated communication channels, information-sharing practices, direct incident reporting mechanisms, and even capacity-building activities are considered as assets since domestic and cross-border cybercrime activities against CI/CII sectors and services have increased exponentially.
CIP/CIIP collaboration initiatives from international organizations
At the United Nations, there are multiple collaborative activities in the CIP/CIIP arena, including (i) those activities organized by the UN Office on Drugs and Crime (UNODC) as part of the Global Program on Cybercrime, which covers the protection of critical infrastructure from terrorist cyberattacks,[30] and (ii) two processes/working groups – the UN Group of Governmental Experts (GGE) and the Open-Ended Working Group (OEWG) – which are currently exploring and addressing the same issue: responsible state behaviour in cyberspace.[31] In 2015, GGE agreed on eleven voluntary norms of responsible state behaviour in cyberspace, an important contribution to establishing how international law applies in cyberspace. Those cybernorms include three specific CIP-related norms: a norm against ICT activity that damages CI; a norm to cooperate and respond to requests for help by states whose CI has been harmed by a cyberattack; and a norm that encourages CIP.
The ITU has been active in promoting CIIP worldwide through the production of relevant reports and papers, organization of regional and national cyberdrills, deployment of the Global Cybersecurity Index (GCI), preparatory activities (for example, CIRT assessments) to establish national CIRTs, organization of capacity-building activities and webinars, and delivery of technical assistance in multiple areas which directly or indirectly benefit the global CIIP.
The World Bank is also committed to providing funding and technical assistance to client countries to strengthen their national cybersecurity capacities. For instance, the World Bank is implementing the Cybersecurity Capacity Maturity Model (developed by the University of Oxford’s Global Cyber Security Capacity Centre) in multiple countries. The World Bank also deploys multiple development projects worldwide to strengthen the cyber-resilience of critical infrastructures in the ICT and financial sectors.
Conclusion
Only 45 per cent of countries worldwide have adopted, at least, baseline CIIP programmes and regulatory frameworks,[32] which represents that the great majority of the global CII’s services are suboptimally protected. Therefore, this good practice guidance also aims to raise awareness and encourage countries and coordinating authorities, mainly ICT regulators, and other stakeholders, to start discussion at the national level and plan for the adoption of comprehensive CIIP programmes and regulatory frameworks to enhance the cyber-resilience of CI/CII sectors and assets.
In the meantime, CIIP coordinators, including ICT regulators, play an important role. As noted above, they should consider establishing and enforcing, at least, minimum requirements to protect and enhance the cyber-resilience of CI/CII sectors and services. Sectoral regulators may not even have the appropriate technical expertise and tools, resources, and a specific legal mandate to monitor and supervise cybersecurity aspects; however, they can deploy some regulatory activities in collaboration with other key stakeholders (for example, national CSIRT, law enforcement agencies), to ensure the continuity of the operation and delivery of services, which is indeed part of their core regulatory functions.
Until these regulatory issues are adequately addressed, including the adoption of robust CIP/CIIP regulatory frameworks, which cover at least the security requirements and legal obligations mentioned above, and real incentives to comply with that regulatory framework, it is unlikely that countries will be able to provide a high level of assurance that CI/CII assets within their territory are adequately protected and cyber-resilient.
Endnotes
- Operation Technology (OT) refers to the hardware and software used with the automation controls systems within infrastructure. OT networks and systems including, Industrial Control Systems (ICS) or Supervisory Control and Data Acquisition (SCADA) are used in multiple industries such as power, oil and gas, water treatment, transportation, defence, traffic control and even within private facilities to monitor and control functions such as heating and cooling (available here). ↑
- According to new a new report from ABI Research, cybersecurity spending for critical infrastructure (CI) will increase by USD9 billion over the next year to reach USD105.99 billion in 2021. available here. (accessed June 4, 2021) ↑
- U.S. Election Assistance Commission. 2017. CI Scoop: History of Critical Infrastructure Designation. available here. ↑
- Council Directive 2008/114/EC on the identification and designation of European critical infrastructures and the assessment of the need to improve their protection. available here. ↑
- CISA (2021). Critical Infrastructure Sectors. available here ↑
- Draft of 2020 CMM Review in Malawi implemented by the World Bank. ↑
- Centre for the Protection of National Infrastructure (2021). Critical National Infrastructure. available here ↑
- Australian Government. Department of Home Affairs (2021). Critical Infrastructure Resilience. available here ↑
- Decree No. 10.222 – 5 of February 2020. available here ↑
- U.S. Election Assistance Commission. 2017. CI Scoop: History of Critical Infrastructure Designation. available here. ↑
- Canada’s National Strategy for Critical Infrastructure. available here. ↑
- CIPedia. 2021. Critical Information Infrastructure. available here. ↑
- EU Directive 2016/1148 on concerning measures for high common level of security of network and information systems across the union. available here. ↑
- OECD. 2019. Recommendation of the Council on Digital Security of Critical Activities. available here. ↑
- US Homeland Security. 2013. NIPP – Partnering for Critical Infrastructure Security and Resilience. available here. ↑
- The ransomware attack involved servers at University Hospital Dusseldorf. available here. ↑
- Australian Government. Department Home Affairs. Protecting Critical Infrastructure and Systems of National Significance. available here. ↑
- ITU World Telecommunication/ICT Regulatory Database. ↑
- BW-CIRT. available here. ↑
- Scarfone, Karen, Dan Benigni and Tim Grance. Cybersecurity Standards. available here. ↑
- European Agency for Cybersecurity. EU Cybersecurity Certification Framework. available here. ↑
- CISA. Traffic Light Protocol. available here. ↑
- European Commission. Revised Directive on Security of Network and Information Systems (NIS2). available here. ↑
- Cyber Security Agency of Singapore. Media Factsheet: Keeping our Digital Spaces Safe. available here. ↑
- National Critical Information Infrastructure Protection Centre. Responsible Vulnerability Disclosure Program. available here ↑
- CISA. Cyber Incident Response. available here ↑
- Malaysian National Cyber Security Agency. National Cyber Crisis Management Plan. available here ↑
- The Network and Information Systems Regulations. 2019. available here ↑
- Cybersecurity Act of 2018. available here ↑
- UNODC. Legislation and International Cooperation to Protecting CNI. available here ↑
- Unpacking the GGE’s Framework on Responsible State Behaviour: Cyber Norms. available here. ↑
- ITU World Telecommunication/ICT Regulatory Database. ↑
References
Assaf, Dan. 2008. “Models of Critical Information Infrastructure Protection.” International Journal of Critical Infrastructure Protection 1: 6-14. https://www.academia.edu/2114887/Models_of_critical_information_infrastructure_protection.
Boyens, Jon, and others. 2021. NIST. Key Practices in Cyber Supply Chain Risk Management: Observations from Industry. NISTIR 8276. https://doi.org/10.6028/NIST.IR.8276.
Brunner, Elgin M., and Manuel Suter. 2008. International CIIP Handbook 2008/2009. Center for Security Studies, ETH Zurich. https://css.ethz.ch/content/dam/ethz/special-interest/gess/cis/center-for-securities-studies/pdfs/CIIP-HB-08-09.pdf.
Burnett, Peter. 2016. The Critical Importance of CIIP to Cybersecurity. https://www.itu.int/en/ITU-D/Regional-Presence/Europe/Documents/Events/2016/Cybersecurity%20Forum%20Bulgaria/GFCE-MERIDIAN%20CIIPv2%20REV.pdf.
CSA (Cyber Security Agency of Singapore). 2019. Guide to Conducting Cybersecurity Risk Assessment for Critical Information Infrastructure. https://www.csa.gov.sg/-/media/csa/documents/legislation_supplementary_references/guide_to_conducting_cybersecurity_risk_assessment_for_cii.pdf
DCMS (Department for Digital, Culture Media and Sport). 2018. Security of Network and Information Systems. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/677065/NIS_Consultation_Response_-_Government_Policy_Response.pdf
Duane, Verner, Frederic Petit, and Kibaek Kim. 2017. “Incorporating Prioritization in Critical Infrastructure Security and Resilience Programs.” Homeland Security Affairs 13, Article 7. https://www.hsaj.org/articles/14091.
ENISA (European Agency for Cybersecurity). n.d. Baseline Capabilities of National Governmental CERTs. Part 2: Policy Recommendations. https://www.enisa.europa.eu/publications/baseline-capabilities-of-national-governmental-certs-policy-recommendations/at_download/fullReport#:~:text=Therefore%20a%20national%20%2F%20governmental%20CERT,the%20public%20and%20private%20sectors.
ENISA (European Agency for Cybersecurity). 2014. Methodologies for the Identification of Critical Information Infrastructure Assets and Services. https://www.enisa.europa.eu/publications/methodologies-for-the-identification-of-ciis/at_download/fullReport.
ENISA (European Agency for Cybersecurity). 2019. Study on CSIRT Landscape and IR capabilities in Europe 2025. https://www.enisa.europa.eu/publications/study-on-csirt-landscape-and-ir-capabilities-in-europe-2025 .
Garcia Zaballos, Antonio and Inkyung Jeun. 2016. Best Practices for Critical Information Infrastructure Protection. Experiences for Latin America and the Caribbean and Selected Countries. Inter-American Development Bank. https://publications.iadb.org/publications/english/document/Best-Practices-for-Critical-Information-Infrastructure-Protection-(CIIP)-Experiences-from-Latin-America-and-the-Caribbean-and-Selected-Countries.pdf.
Giannopoulos, Georgios, Roberto Filippini, and Muriel Schimmer. 2012. Risk Assessment Methodologies for Critical Infrastructure Protection. Part I: A State of the Art. Ispra: European Commission, Joint Research Centre, Institute for the Protection and Security of the Citizen. https://publications.jrc.ec.europa.eu/repository/bitstream/JRC70046/lbna25286enn.pdf.
INSA (Intelligence and National Security Alliance). 2018. Managing a Cyber Attack on Critical Infrastructure: Challenges of Federal, State, Local and Private Sector Collaboration. https://www.insaonline.org/wp-content/uploads/2018/08/INSA-Managing-Cyber-Attack-Critical-Infrastructure.pdf.
INTERPOL. 2020. COVID-19 Cybercrime Analysis Report. https://www.interpol.int/en/News-and-Events/News/2020/INTERPOL-report-shows-alarming-rate-of-cyberattacks-during-COVID-19.
ITU (International Telecommunication Union). 2021. Global Cybersecurity Index v4. Geneva: ITU. https://www.itu.int/en/ITU-D/Cybersecurity/Pages/global-cybersecurity-index.aspx.
ITU, World Bank and partners. 2021. Guide to Developing a National Cybersecurity Strategy. https://ncsguide.org/the-guide/lifecycle/.
NERC (North American Electric Reliability Corporation). 2020. Cyber Security Supply Chain Risk Management Plans. Implementation Guidance for CIP-013-1. https://www.nerc.com/pa/comp/Pages/Supply-Chain-Risk-Mitigation-Program.aspx.
OECD (Organization for Economic Cooperation and Development). 2019. Good Governance for Critical Infrastructure Resilience. OECD Review of Risk Management Policies. https://www.oecd-ilibrary.org/sites/02f0e5a0-en/index.html?itemId=/content/publication/02f0e5a0-en&_csp_=eb11192b2c569d5c3d1424677826106a&itemIGO=oecd&itemContentType=book.
Skeath, Caleb. 2018. “FERC Approves New Cybersecurity Standards for Supply Chain Risk Management.” National Law Review, October 26, 2018. https://www.natlawreview.com/article/ferc-approves-new-cybersecurity-standards-supply-chain-risk-management.
TNO. 2017. The GFCE-Meridian Good Practice on Critical Information Infrastructure Protection for Governmental Policy-Makers. https://www.tno.nl/media/8578/gpg_criticalinformationinfrastructureprotection.pdf.
UNOCT (United National Office for Counter-Terrorism). 2018. The Protection of Critical Infrastructure against Terrorist Attacks: Compendium of Good Practices. https://unrcca.unmissions.org/sites/default/files/eng_compendium-cip-final-version-120618_new_fonts_18_june_2018_optimized.pdf.
Last updated on: 19.01.2022